Fastvue blog
Fixing SSL Decryption Issues in Palo Alto PAN-OS 10
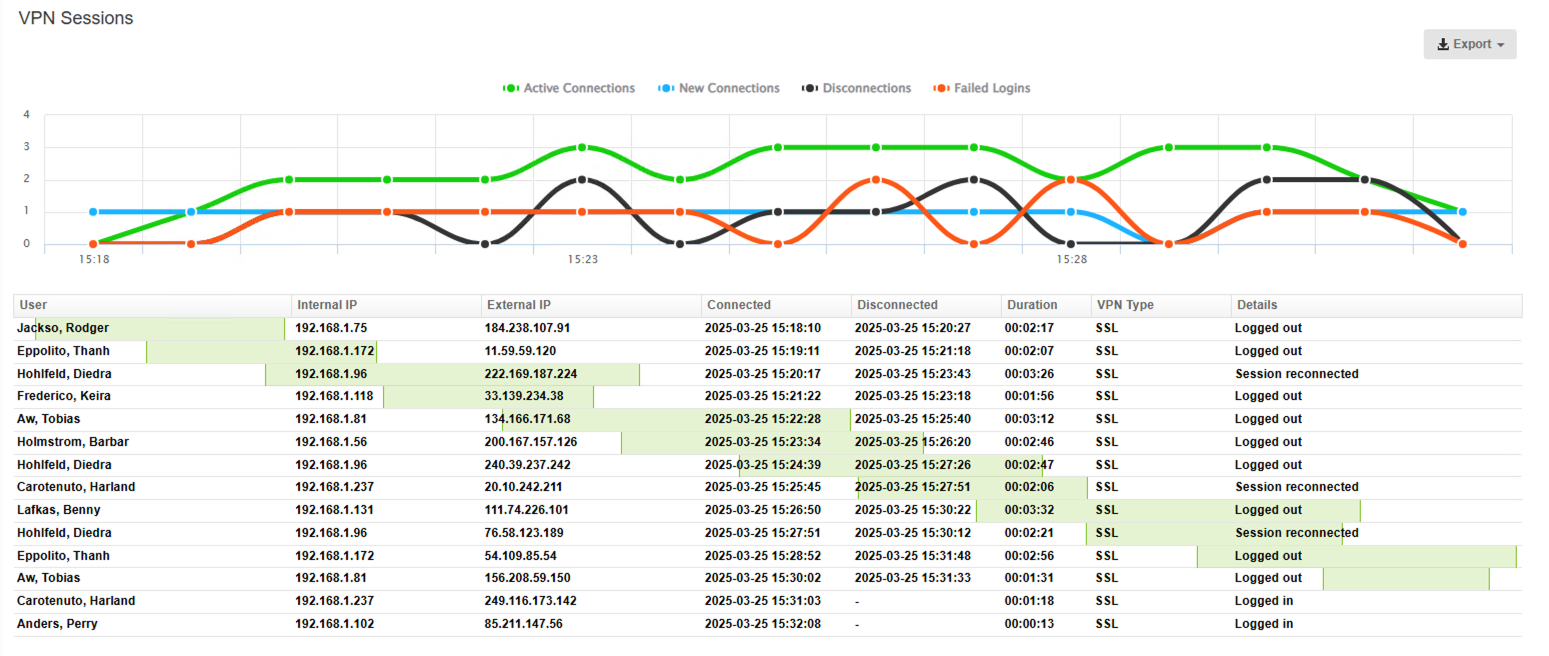
Introducing SonicWall VPN Reports and VPN Dashboard
Simplify Forefront TMG Migration By Web Chaining To An Upstream Proxy
How Digital Monitoring for Schools Helps Protect Students Online (2025 Update)
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)
Sophos XG - How to Block Searches and URLs with Specific Keywords
Using Sophos XG's XStream DPI Engine While Enforcing SafeSearch and YouTube Restrictions
Introducing Fortinet FortiGate VPN Reports and VPN Dashboard
Introducing Sophos XG VPN Reports and VPN Dashboard
7 Key Configurations To Optimize Fortinet FortiGate's Logging and Reporting
Remote Working: 8 Tips for IT Security Teams
Fastvue and Sophos Working Together To Keep Students Safe Online (Product Demo)
3 Signs You've Hired The Wrong Person
How Much Time Are Your Employees Wasting on the Internet?
Reporting on Employee Internet Usage During Work Hours
SonicWall Analyzer End of Life and SonicWall Analytics Review
Reporting on Internet Usage Productivity with Fortinet FortiGate
A Crazy Six Months at Fastvue. Report Speed, Safeguarding, FortiGate and More!
Fastvue Reporter with Faster Reports and New Report Types is Now Available!
Attacking and Testing Sophos SG Web Application Firewall
Attacking and Testing Sophos XG Web Application Firewall
New Version of Fastvue Reporter with Faster Report Times (Beta)
Fastvue Syslog Version 2.0 Now Available! A Free Syslog Server for Windows
Testing Web Application Firewalls with Web Security Dojo
Network Troubleshooting with Sophos UTM tcpdump Packet Captures
How To Retrieve Log Files From a Sophos UTM Cluster Slave Node
How To Deploy Fastvue Reporter in a High Availability Cluster
How To Configure Sandboxing with Sophos Sandstorm
Troubleshooting Sophos UTM Up2Date Failure Due to Disk Space
How Google's QUIC Protocol Impacts Network Security and Reporting
Sophos SG and Amazon VPC VPN Setup and Testing Guide
How Fastvue is Ensuring GDPR Compliance
How To Receive an Alert when SonicWall's WAN Interface Link Goes Down
Recategorizing Websites in Sophos XG and Reclassifying Productivity
School Cyber-safety and Pastoral Care – Web Usage Monitoring for Schools
Testing Sophos SSL VPN Performance - UDP or TCP?
Using Sophos XG Packet Capture To Troubleshoot Connectivity Issues
Sophos STAS Authentication Step by Step
Improving the Performance of Sophos XG's Intrusion Prevention System (IPS)
Configuring a Site-to-Site VPN Between Sophos UTM (SG) and Sophos XG
The Best SonicWall Configuration for Detailed Logging and Reporting
Using Sophos UTM's Request Redirection Feature in v9.5
Sophos XG and SG (UTM) SSL Site-to-Site VPN Compatibility
SonicWall Reporting on Users, Departments and AD Security Groups
SonicWall Logging Issues Affecting Alerts and Reports on Google Searches
SonicWall DPI-SSL Logging Issues Affecting Bandwidth Reports
How to Configure Sophos XG's Free Dynamic DNS Service
Repurposing Sophos Hardware as a Multifunctional Virtual Server
Create Real-time Alerts for WannaCry Ransomware Infected Machines
Reporting on WannaCry Ransomware Infected Machines
Create Real-time Alerts for WannaCry Ransomware Infected Machines (Sophos)
Reporting on WannaCry Ransomware Infected Machines
Sophos XG Reporting Now Available in Fastvue Sophos Reporter!
SonicWall SonicOS Enhanced 6.2.7.1 - Now with Referrer URLs!
Filtering and Forwarding Sophos UTM Syslog Data with Syslog-ng
How to Configure Multiple Site-to-Site SSL VPNs with Sophos UTM
Monitoring Web Searches to Prevent Radicalisation and Extremism
Easy WAN Emulation for Application Testing
Configure a URL Redirect with Sophos UTM's Web Application Firewall
Force Sophos UTM to Log User Information for Scanned File Downloads
SonicOS 6.2.6.0-20n New CFS and New Logging Bugs
SonicWALL's 'Not Rated' Syslog Bug and Workaround
Deploying Endpoint Protection Web Control with Sophos UTM
Deploying Endpoint Protection with Sophos UTM and Enterprise Console
Active Directory SSO Authentication in Transparent Proxy Mode
How Google Data Saver Affects Security, Privacy and Reporting
The Role of HTTPS Inspection in Google Search and YouTube Reports
How To Remove False Positives in Sophos UTM's Web Application Firewall
How to Accurately Monitor and Improve Sophos UTM CPU Performance
How To Install Fastvue Reporter on your SonicWALL Analyzer or GMS Server
Introducing Fastvue Reporter for SonicWALL. SonicWALL Reporting Made Awesome!
Publishing PowerShell over SSH Using Sophos UTM's HTML5 VPN Portal
Overcoming Sophos UTM HA Cluster Logging and Reporting Issues
How To Secure Your UTM With Sophos UTM Access Control
How To Allow Skype Through Sophos UTM in Standard Proxy Mode
Finding a Forefront TMG replacement is more urgent than you thought
Implementing Exceptions in Sophos UTM Without Relaxing Security
Two Factor Authentication with Sophos UTM - For Users
Two Factor Authentication with Sophos UTM – For Administrators
Two Factor Authentication with Sophos UTM - Concepts and Considerations
Sophos RED 10 vs RED 50 - A Detailed Feature Comparison
Unlocking Sophos UTM's DHCP Capabilities
A Simple Guide To Deploying A Site To Site VPN Using Sophos UTMs
Sophos RED Deployment Modes Explained - Choosing The Right One For You
Easily Evaluate Sophos UTM 9.3 Using Full Transparent Mode
Sophos UTM DSL PPPoE Interface Explained
Switch Between Windows Server Core and Full GUI - The Easy Way
Malvertising And Why You Should Ad-block Your Network At The Gateway
Limit Runaway YouTube Traffic With Sophos UTM QoS
Introduction to Sophos SUM (Sophos UTM Manager)
Block Sites Signed By Untrusted Certificate Authorities On Sophos UTM
Setup a Sophos UTM SSL VPN In 7 Simple Steps!
Introducing Fastvue Sophos Reporter for Sophos Web Appliance (Beta)!
How to Use Sophos UTM Uplink Balancing to Achieve ISP Redundancy
What You Really Need To Know About EV Certificates
How To Connect Remote Networks with Sophos RED Devices
How to Configure Dynamic DNS on Sophos UTM
Easy DIY Home Internet Monitoring System with Sophos UTM and Fastvue
How HTTPS / SSL Inspection Affects Logging and Reporting in Sophos UTM
Fastvue TMG Reporter v3.0 Out Now!
How To Secure Fastvue TMG Reporter for Private Report Sharing
Fastvue Sophos Reporter v2.0 Out Now!
How To Secure Fastvue Reporter for Private Report Sharing
Reporting on Website Usage Including Content From CDNs
Creating Your Own Sophos UTM Bootable USB Installation Drive
How to Fix Web Application Proxy and AD FS Certificate Issues (Error Code 0x8007520C)
Fastvue Sophos Reporter 2.0 Beta Now Available
Fastvue TMG Reporter 3.0 Beta Now Available
Sophos UTM Auto Proxy Configuration - 3 Simple Steps
Easily Evaluate Sophos UTM Using Full Transparent Mode
Sophos UTM Operation Modes: Standard, Transparent vs Full Transparent
Why Web Reporting is the Big Winner in Sophos UTM 9.3
Updated Exchange 2013 Forms Based Authentication Templates for TMG
Never Miss Reporting Data With Sophos UTM's Remote Log Archive
Troubleshooting Sophos UTM's Remote Log Archive Feature
The Bandwidth Impact of Apple's iOS 8 Release On Your Network
How to Backup, Upgrade and Recover Sophos UTM Offline
Understanding Hyper-V Dynamic Memory (Dynamic RAM)
Replacing Forefront TMG with Sophos UTM (Webcast)
How To Publish Websites with Sophos UTM Web Server Protection
How to Build a Sophos UTM High Availability (HA) Cluster in Hyper-V
Sophos UTM and Active Directory Step by Step Integration Guide
Forefront TMG HTTPS Inspection Issues with SHA256 / CNG Certificates
How to Enable and Disable SSL / TLS Versions on Forefront TMG
How To Allow Sites During Certain Times With Sophos UTM
Six Reasons Why You Need Sophos Reporter Over Sophos UTM’s Reporting
How to Deploy Sophos UTM on Hyper-V in 7 Simple Steps
How To Access Blocked Sites Using Google Web Cache, And How To Prevent It With Sophos UTM
We've Launched! Fastvue Sophos Reporter Is Now Available
How To Secure The Fastvue Sophos Reporter Web Site
How to Reset Sophos UTM Passwords (WebAdmin, Root and Loginuser)
How To Extend Forefront TMG's Web Protection Services (WPS) After November 30 2012
The Ins and Outs of Bi-directional Firewall Rules
Forefront TMG Forms Based Authentication Template for Exchange 2013 OWA
How To Solve "13 The Data Is Invalid" Error in Forefront TMG
Make The World A Better Place with Fastvue and Microsoft Reputation Services (MRS)
How To Recover Forefront TMG From a Corrupt Configuration Database
Forefront TMG Configuration Backup Scripts For Standalone and Enterprise Arrays
Understanding Hyper-V CPU Usage (Physical and Virtual)
Deploying Winfrasoft Forefront TMG Virtual Appliances
Fastvue TMG Reporter Voted Best Reporting Application - ISAServer.org Readers Choice
Monitoring, Alerting and Blocking Countries with Forefront TMG
Troubleshooting Forefront TMG Web Proxy Auto Discovery (WPAD) Issues
How to Report on YouTube Activity with Fastvue TMG Reporter
What everyone should know about HTTPS, SSL, TLS and Certificates
Forefront TMG Tips and Tricks
TMG Reporter 2.1 Out Now!
HTTPS Inspection in Forefront TMG - Concerns and Misconceptions
How To Purchase Forefront TMG After January 2013
Reducing Anonymous (Unauthenticated) Traffic in Forefront TMG
TMG Reporter 2.1 Now Available
Free Windows Grep for W3C Log Files
Extending Forefront TMG's ISP Redundancy Features
Reporting on Hostnames with Forefront TMG SecureNAT Clients
Fastvue Acquires WebSpy
Forefront TMG Web Chaining and Reporting
Critical Update for TMG Reporter (2.0.1.21)
Hunting IE6 Zombies with TMG Reporter
Blocking Sites with Forefront TMG
Our Five Most Common Forefront TMG Reporting Questions
New TMG Reporter Features: Custom Reports, SQL Support and more
Testing and Monitoring Forefront TMG Malware Inspection and Intrusion Prevention (NIS) Systems
Hosting Multiple Web Sites On A Single Host with IIS and Forefront TMG
Mitigate DNS Exploits with Forefront TMG
Forefront TMG End Of Life and What It Means For TMG Reporter
Mobile Friendly Forefront TMG Forms Based Authentication Template
Block Instant Messaging Traffic Using Forefront TMG's HTTP Filter
Everything You Need To Know About User Agents
Monitor Bandwidth and Limit Internet Speed in Forefront TMG 2010
Deploying TMG Reporter on Virtual Machines and Monitoring Server Performance
How To Fix Windows Live Messenger 2011 Forefront TMG Login Issues
Useful Scripts to Disable Logging for System Policy Rules in Forefront TMG 2010
How to Configure Forefront TMG Malware Alerts
How To Secure And Publish the Fastvue TMG Reporter Web Site
How Kerberos and CARP Affect Forefront TMG Reporting
The Microsoft Forefront TMG Firewall service terminated unexpectedly. It has done this
Customizing Website Categories with Forefront TMG URL Filtering
Reporting on Celestix MSA Threat Management Gateway Appliances
Forefront TMG Enterprise Logging with Remote SQL Server
Reporting on Forefront TMG's Remote SQL Database
Tips for Healthy Logging and Reporting in Forefront TMG 2010
How to Manage Forefront TMG's Cache with CacheDir
Enterprise Reporting Challenges with Forefront TMG 2010
Fastvue TMG Reporter's System Requirements Explained
Logging Improvements in Forefront TMG 2010
The Best Forefront TMG Configuration for TMG Reporting
TMG Reporter 2.0 Is Here!
Fastvue TMG Reporter Beta Update 2.0.0.12
TMG Reporter Beta Update (2.0.0.10)
TMG Reporter Beta (Update 2.0.0.7)
Announcing Fastvue TMG Reporter Version 2.0 Beta
Discover what is going on in your home network. Simply.
How to find which Forefront TMG Service Pack is installed
How We Designed The Fastvue Dashboard
Fastvue for TMG receives Silver Award on ISAServer.org
Installing and Configuring Microsoft Forefront TMG - Videos
The Truth About the Anonymous User
We've Launched!!!
Tell Us What You Think!
Our Support Center is Live!
New Fastvue for TMG Build Available