How To Configure Sandboxing with Sophos Sandstorm
by

Etienne Liebetrau
Sandboxing with Sophos Sandstorm is an enterprise-level firewall feature that has become very popular recently and for good reason. This feature is now available on Sophos SG (UTM), XG and Web Appliance. In this article, I will go through setting up Sophos UTM to enable Sandboxing with Sophos Sandstorm. Then I'll step through what happens when it is triggered. I’ll also go into details about the user’ experiences, the background process and of course tracking the events in the log files.
When it comes to Sandboxing, there are as many names as there are vendors, including Sophos Sandstorm, Check Point SandBlast, Fortinet FortiSandbox, Palo Alto WildFire, and SonicWall Capture ATP. They all work on the same basic principles.
Although many firewalls and proxies have had malware protection for a long time, it has been signature-based detection. This means that the file is downloaded, checked against a known list of malware, and then either passed or denied. This is very effective against known threats. But as we have seen with traditional desktop AV, this has been a losing race for a while.
Enter Sandboxing, or in Sophos’s case, cloud-based Sandboxing. When sandboxing with Sophos Sandstorm, a suspicious file is uploaded to Sophos' sandboxing servers where it is 'detonated', its behavior analyzed and it is either convicted or acquitted for containing malware.
Detonating a file sounds dangerous, so what does it mean? Well, in the case of a EXE it means running it in an emulated environment, an MSI file gets installed and then executed, ZIP files are extracted and executables are executed and so on.
The quality of the system emulation and the monitoring and analysis is of key importance. This is why having it as a cloud service makes more sense than trying to cram that amount of functionality into the firewall itself. Sandboxing shifts malware detection from being signature based, to being based on behavioral analysis.
Configuring Sandboxing on Sophos UTM
Sandstorm is an additional feature that requires separate licensing. The best bet to get this tested is to reach out to your local Sophos partner and arrange a trial. Since it enhances the security of the Web Protection and or Email protection, one or both of these modules have to be licensed. Note that the features described below pertain to Sophos UTM 9.5 onward since they added some additional enhancements.
If you don’t already have an entitlement for Sandstorm get the license file and activate it under the following section:
- In Sophos UTM's Web Admin interface, go to Management | Licensing | Installation
- Upload the new license file
- Click Activate
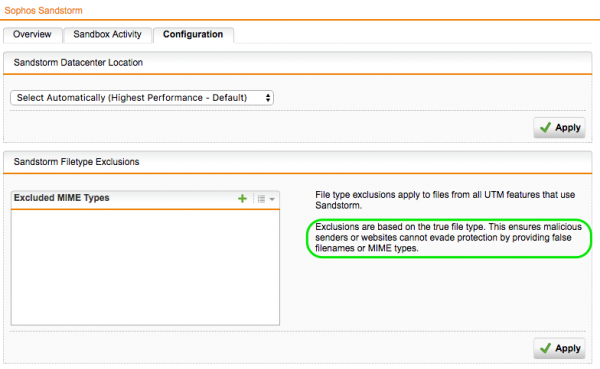
Sandstorm itself is remarkably simple to configure. Just go to Advanced Protection | Sophos Sandstorm | Configuration
From here you can select the cloud datacenter location closest to you or let it automatically continually evaluate them and pick the best one for you.
Optionally you can also exclude MIME types. Keep in mind that by default, at this stage, Sandstorm will only evaluate the following:
- PE and EXE files, including 32 or 64-bit programs, and 32 and 64-bit DLLs
- Microsoft Office Word Documents with file extensions of .doc, .docx, .docm, or .rtf
- Microsoft Office Excel Documents with file extensions of .xls, .xlsx, or .xlsm
- Microsoft Office PowerPoint documents with file extensions of .ppt, .pptx, or .pptm
- PDF documents (.pdf)
- PDF XML documents (.xpf)
- ActiveMime
- Archives (ZIP, BZIP, GZIP, RAR, TAR, LHA/LZH, XZ)
Note this is based on the true file type. This ensures malicious senders or websites cannot evade protection by providing false filenames or MIME types.
Activate Sophos Sandstorm
Since it is an enhancement to the Web protection module we need to make some changes there too:
- Find the relevant or default Content filter profile
- Select the Antivirus Tab
- Check the Use antivirus scanning checkbox.
- Check the box Refer suspicious items to Sophos Sandstorm
Did you know: Fastvue Sophos Reporter produces clean, simple, web usage reports using log data from your Sophos UTM that you can confidently send to department managers and HR team.
Sophos Sandstorm's End User Experience
Let’s see what happens when we download a file that requires additional scanning.
Step 1: Sophos UTM Intercept's the file
The UTM intercepts the download and shows us the downloading screen.
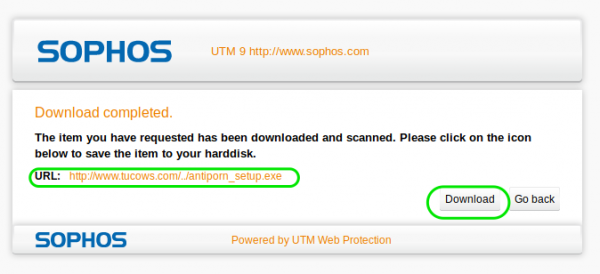
Step 2: File requires further analysis
When the download completes we get another screen stating that the File Require Further Analysis with a link to see more details.
Step 3: Sophos Sandstorm Analysis In Progress
The Sophos Sandstorm Analysis in progress screen will keep refreshing. This may take several minutes.
Step 4: Sophos Sandstorm Analysis Complete
The Analysis completes and the download is presented to the browser.
The sequence we just saw is one of many possible outcomes. In the background, what happens is the following decision structure:
- Anti-virus engine scan files to determine if there is already knowledge about the file.
- The file is determined as known good, known bad or unknown.
- Known bad files are blocked, known good files are released to the end-user.
- For unknown files, depending on the file anti-virus will determine if the file has any active content (e.g. Macros in Office documents or JavaScript in pdfs).
- If there is no active content the file is considered safe and released to the end-user.
- If active content is detected, a hash value of the file is sent to Sandstorm to check if this file has previously been analyzed.
- If the file has previously been analyzed a result is sent back. If it is malicious, the file will be blocked. If safe, the file is released to the end-user.
- If the file is unknown by Sandstorm and there is active content, the file will be uploaded to Sophos Sandstorm and detonated for further analysis. If the file is malicious, the file will be blocked. If safe, the file is released to the end-user.
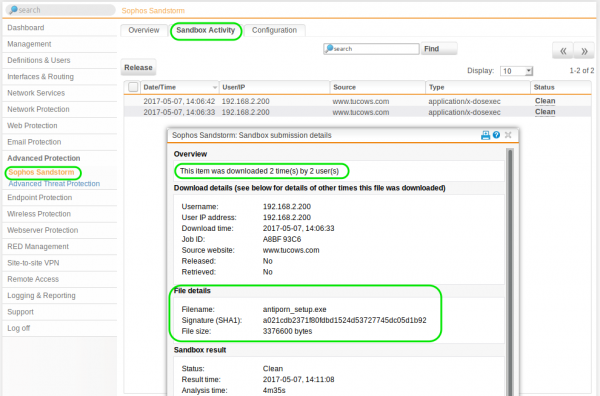
To keep track of what is happening from a Sandstorm perspective you can check the Sophos console under the Advanced Protection section.
In this case, you can see two suspicious files but only two were sent for analysis. You can also see that the time taken is nearly 5 minutes, it is not insignificant as far as user impact is concerned. The reason only two were sent is that I downloaded each suspicious file twice. Only the first instance was sent, the second was compared and released immediately.
For the second download the user would see the usual two step download scan and download screens.
To see some more details on the files and also potentially release a file deemed malicious you can go to Advanced Protection | Sophos Sandstorm | Sandbox Activity.
Sophos Sandstorm Log Analysis
These various activities we have also show up in the http.log file. Since the addition of Sandstorm, an additional "sandbox" field has been added to the log. Typically the following values are observed:
- sandbox="-“ SAV engine has determined the file should not be sandboxed. The file was not sent to the cloud.
- sandbox="1" SAV engine has determined the file should be sandboxed. The system is not configured to sandbox the file. The file was not sent.
- sandbox="2" The file was sent to the cloud for further investigation. Results are pending.
- sandbox="3" Sandbox considers the file safe and it is allowed. The file was not sent to the cloud.
- sandbox="4" Sandbox considers the file safe and it is allowed. The file was sent to the cloud.
If the file is sent to the cloud, there are two log lines. The first is =2 and the second is the final value which would either be 3 or 4
Here are the log entries from the testing done throughout the article.
2017:05:07-14:06:34 et-hom-lab-utm httpproxy
[5041]: id="0090" severity="info" sys="SecureWeb" sub="http" name="web request blocked" action="sent to sandbox" method="GET" srcip="192.168.2.200" dstip="64.99.128.15" user="" group="" ad_domain="" statuscode="403" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="0" request="0xdf8bc000" url="http://www.tucows.com/download/windows/files1/**antiporn\_setup.exe**" referer="" error="" authtime="0" dnstime="1" cattime="178340" avscantime="2029134" fullreqtime="12957055" device="0" auth="0" ua="Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:53.0) Gecko/20100101 Firefox/53.0" exceptions="" category="148" reputation="trusted" categoryname="Shareware/Freeware" content-type="application/x-dosexec" jobid="a8bf93c6" sandbox="2"
Followed by the confirmation entry
2017:05:07-14:11:08 et-hom-lab-utm sandboxd[6299]: id="0001" severity="info" sys="SecureWeb" sub="http" name="http access" action="pass" method="GET" srcip="192.168.2.200" dstip="64.99.128.15" user="" group="" ad_domain="" statuscode="200" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="0" request="0xdf8bc000" url="http://www.tucows.com/download/windows/files1/**antiporn\_setup.exe**" referer="" error="" authtime="0" dnstime="1" cattime="178340" avscantime="2029134" fullreqtime="12957055" device="0" auth="0" ua="Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:53.0) Gecko/20100101 Firefox/53.0" exceptions="" category="148" reputation="trusted" categoryname="Shareware/Freeware" content-type="application/x-dosexec" jobid="a8bf93c6" sandbox="4"
If we repeated the test and tried to download the file again we will see only the following entry
2017:05:07-14:14:55 et-hom-lab-utm httpproxy[5041]: id="0001" severity="info" sys="SecureWeb" sub="http" name="http access" action="pass" method="GET" srcip="192.168.2.200" dstip="" user="" group="" ad_domain="" statuscode="200" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="3376600" request="0xdfaf1e00" url="http://www.tucows.com/download/windows/files1/**antiporn\_setup.exe**" referer="http://passthrough.fw-notify.net/static/409533/downloader.html" error="" authtime="0" dnstime="0" cattime="0" avscantime="0" fullreqtime="98368" device="0" auth="0" ua="Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:53.0) Gecko/20100101 Firefox/53.0" exceptions="" category="148" reputation="trusted" categoryname="Shareware/Freeware" content-type="application/x-dosexec" sandbox="3"
Do you need Sophos Sandstorm
Sophos UTM is able to scan the download with either or both of the Sophos or Avira engines, and that happens regardless. The potential problem comes in when Sophos UTM does not find malware. If sandstorm is enabled you get a better second opinion before it is allowed.
You can figure out how often this would have been required by checking the sandbox="1" entries in your logs. From a shell, you can run the following to count them for you. This will give you the suspect count for the day so far.
cat http.log | egrep sandbox=\"1\" | wc -l
One thing to keep in mind is that Sophos UTM can only scan files it can read, this mean HTTPS inspection should be enabled, otherwise, AV Scanning and Sandstorm would only apply to HTTP traffic and not HTTPS. Since we can see that the bulk of traffic today is indeed HTTPS the effectiveness of Sandstorm would largely be affected by this.
Not covered in this article is the fact that this same method of protection is used by mail protection. Since email is a primary vector for Ransomware this is a serious benefit. If you are using Sophos for email sanitation it is a strong recommendation that you get and use it.
Conclusion
Prevention is better than cure. Keeping the new generation of malware threats from entering your environment is key to an in-depth defence strategy. With Sophos Sandstorm, the UTM is now able to offer even better protection and visibility than before, relying less on the client to protect itself.
There is a potential user impact. Sending a file for analysis takes a few minutes, even it is a small file. If the users are not briefed as to why this is required, you may meet some resistance. If however, you protect their family photos from getting Crypto locked, they might appreciate the extra effort.
Now that you have an extra layer of protection for your network, why not improve your web usage reporting by installing Fastvue Sophos Reporter? Fastvue Sophos Reporter consumes syslog data from Sophos UTM (SG) and Sophos XG Firewalls and produces clean, simple, web usage reports that you can confidently send to department managers and HR team. Automate reports and get the job of reporting on web usage off your desk and into the hands of people that need it. Download the 30 day free trial today!
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)
Sophos XG - How to Block Searches and URLs with Specific Keywords