Comparing Fortinet FortiGate’s Flow-based vs Proxy-based Web Filter Options

by

Etienne Liebetrau
Fortinet FortiGate comes with two options for creating and applying web filters in FortiOS. There are Flow-based or Proxy-based web filters. The default web filter mode is Flow-based due to the better performance it promises compared to the traditional Proxy-based filter.
As you can see in the screenshots below, there are more features available when selecting FortiGate’s Proxy-based feature set for your web filter profile as indicated by the red P symbol. But do you need them?
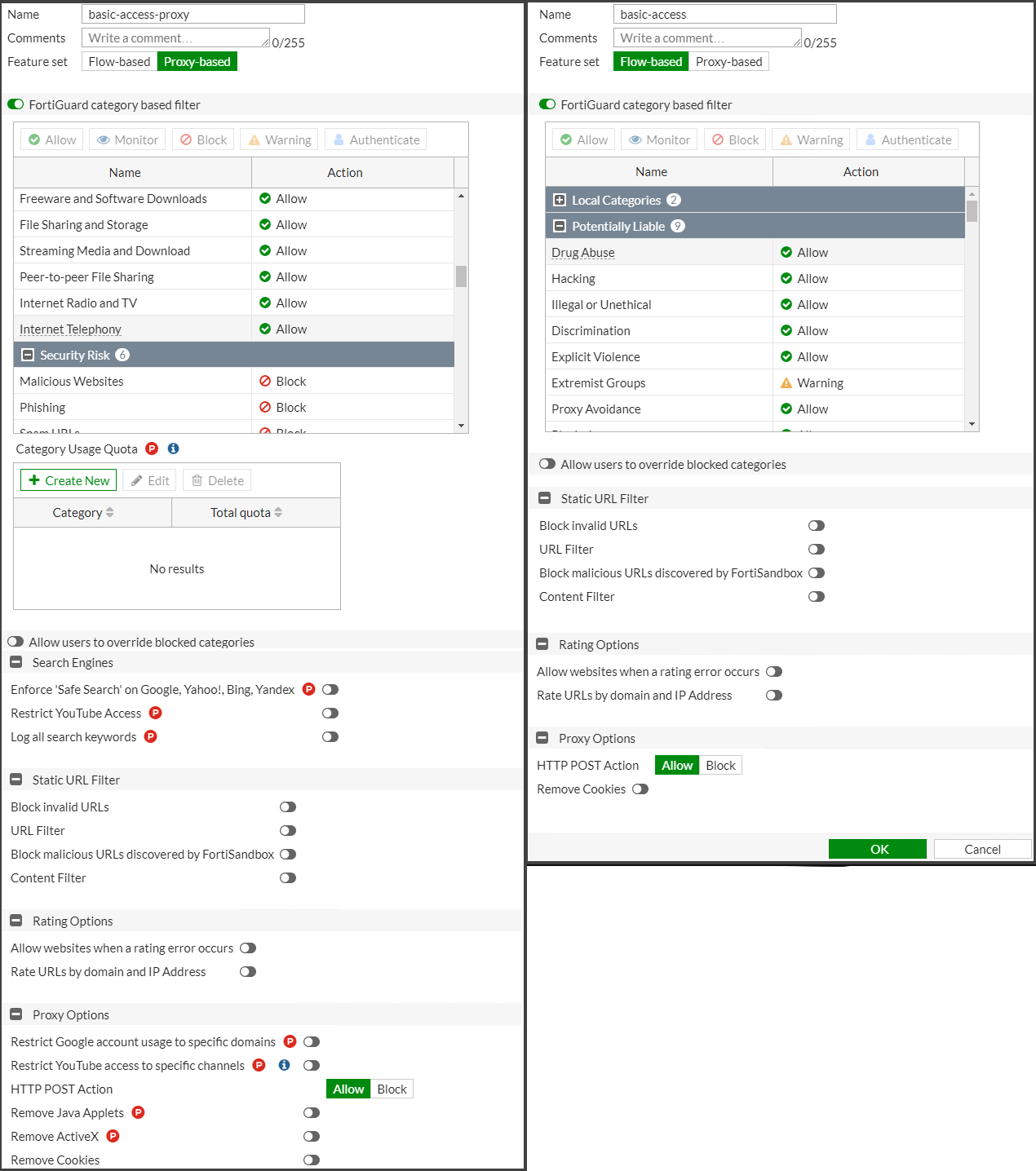
Note that the images above are from FortiOS 6.4.5 and the two YouTube control options have moved to Security Profiles | Video Filter in FortiOS 7.0.
FortiOS 7.0 Proxy-based Web Filter Features Set
Let’s go through each of the additional features available in Proxy-based mode so you can decide for yourself if these additional features justify the performance hit.
Category Usage Quota
In addition to using web categories and overrides to limit user access to URLs, proxy-based web filters also enable you to set a daily quota by category, category group, or classification. Quotas allow access for a specified length of time or a specific bandwidth threshold and are calculated separately for each user. Quotas are reset daily at midnight.
Quotas can be set for the Monitor, Warning, or Authenticate actions. Once the quota is reached, the traffic is blocked and a replacement message page is displayed.
Enforce Safe Search
Fortinet FortiGate’s Enforce Safe Search option applies to popular search sites and prevents explicit websites and images from appearing in search results. The supported search sites are:
Google
Yahoo
Bing
Yandex
Note that this feature also requires Deep Packet Inspection to be enabled.
Log all search keywords
You can use this setting to log all search phrases entered into search engines. This populates the ‘Key Word’ field in FortiGate’s web filter log files. This feature is not needed if you are using Fastvue Reporter for FortiGate, as search terms are extracted directly from the URL field rather than relying on this feature. This also allows Fastvue Reporter for FortiGate to report on searches entered into other non-search engine sites such as YouTube, Amazon and Facebook.
The logging of search keywords by FortiGate as well, as the extraction of search keywords from the URL field by Fastvue Reporter for FortiGate both require Deep Packet Inspection to be enabled.
Restrict Google account usage to specific domains
If you are using GSuite for your company’s email, cloud storage, etc, this setting can allow access to your company’s Google domain and block access to other non-work Google domains and services. Once again, this setting requires Deep Packet Inspection to be enabled.
Remove Java applets and ActiveX
Proxy-based web filter profiles have settings to block Java applets and ActiveX controls. Java Applets and ActiveX are dying technologies and today’s modern web browsers are very good at sandboxing and preventing malicious code from being delivered through these technologies.
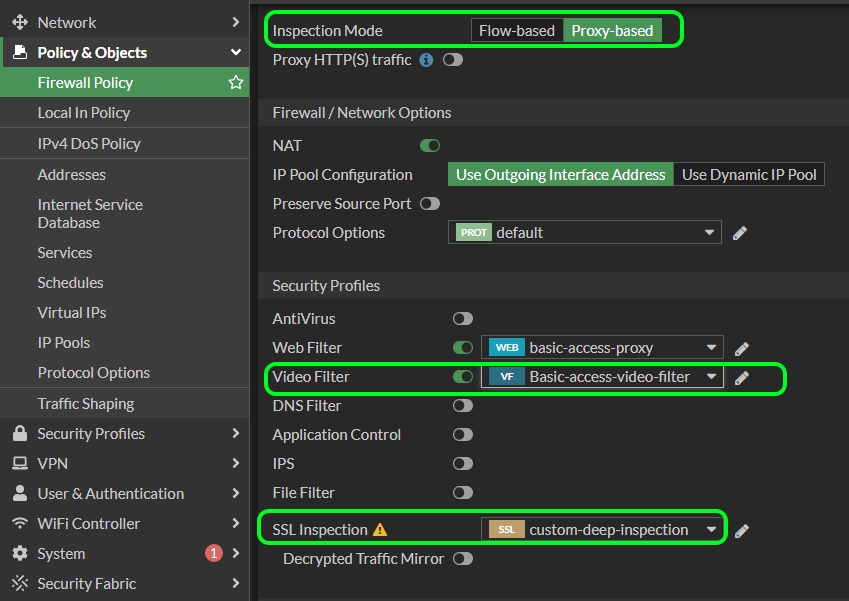
Restricting YouTube Access & the new Video Filter feature in FortiOS 7.0
As mentioned, FortiOS 7.0 moves the two YouTube restriction feature into a separate ‘Video Filter’ option (Security Profiles | Video Filter) that you can apply to your firewall policies alongside web filters. Restricting YouTube Access is particularly important in Schools where teachers may need to whitelist specific YouTube channels.
Video filters are only available to Proxy-based Firewall Policies, and again Deep Packet Inspection is required for this feature to work.
FortiGate’s Proxy-based Web Filter CLI Options
The FortiGate CLI also contains some options that only apply to FortiGate’s proxy-based web filter profiles.
| SETTING | DESCRIPTION |
|---|---|
| wisp | Enable/disable web proxy WISP |
| web-filter-activex-log | Enable/disable logging ActiveX. |
| web-filter-applet-log | Enable/disable logging Java applets. |
| web-filter-jscript-log | Enable/disable logging JScripts. |
| web-filter-js-log web-filter-vbs-log | Enable/disable logging Java scripts. |
| web-filter-unknown-log | Enable/disable logging unknown scripts. |
| web-filter-referer-log | Enable/disable logging logging referrers. |
| web-filter-cookie-removal-log | Enable/disable logging blocked cookies. |
| web-ftgd-quota-usage | Enable/disable logging daily quota usage. |
| web-antiphishing-log | Enable/disable logging of AntiPhishing checks. |
The following options are available for all web filters (proxy or flow-based).
| SETTING | DESCRIPTION |
|---|---|
| log-all-url | Enable/disable logging all URLs visited. |
| web-content-log | Enable/disable logging logging blocked web content. |
| web-filter-command-block-log | Enable/disable logging blocked commands. |
| web-filter-cookie-log | Enable/disable logging cookie filtering. |
| web-url-log | Enable/disable logging URL filtering. |
| web-invalid-domain-log | Enable/disable logging invalid domain names. |
| web-ftgd-err-log | Enable/disable logging invalid domain names. |
| extended-log | Enable/disable extended logging for web filtering. |
For Fastvue Reporter for FortiGate, we recommend enabling the following CLI options for either proxy-based or flow-based profiles:
config webfilter profile
edit {name-of-profile}
set web-content-log enable
set extended-log enable
set web-extended-all-action-log enable
-- repeat for all web filter profiles --
endNote: The extended-log option adds useful information into the ‘rawdata’ field, but ensure your syslog server in FortiGate is configured to use the ‘reliable’ option (sending syslog over TCP instead of UDP), otherwise the extra information will get truncated to 2kb.
For proxy-based profiles, we recommend enabling the following additional option:
config webfilter profile
edit {name-of-profile}
set web-filter-referer-log enable
-- repeat for all proxy-based web filter profiles --
endNote that referrer URLs are logged in flow-based mode by the ‘extended-log’ option, even though there is no explicit option to enable them as there is in proxy-based mode.
Conclusion
Both methods of applying web filters can be very effective at managing your web filtering and hopefully, the explanations above help you choose which web filter option you should choose. For example, the education sector often considers enforcing Safe Search as an essential feature for students, and this is only available through proxy-based web filters. Other proxy-based features are no longer considered essential, as technologies such as ActiveX become obsolete.
I highly recommend spending some time with the available options and then picking your preferred method, as ‘more options’ doesn’t necessarily mean ‘better for you’. Regardless of the method you choose, both support a detailed amount of logging (when enabled) that allows Fastvue Reporter for FortiGate to accurately report on your web usage.
Why not get started with the fully-featured 30-day trial!
Resources
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn