HTTPS Inspection in Forefront TMG - Concerns and Misconceptions
by

Etienne Liebetrau
When configuring your Forefront TMG Web Access policy, there is an option to enable HTTPS inspection. In this article, I will aim to clear up some confusion surrounding HTTPS inspection in Forefront TMG, and the impacts it has on URL filtering, privacy and reporting.
The Tunnel
We all know that HTTPS traffic is encrypted. A virtual secure tunnel is created between the client and the server over which the “payload” of the conversation is transmitted, but it is important to know that the 'control data' is not encrypted.
To illustrate this, you can look at a WireShark capture of an unencrypted HTTP browser session. Here you can see the server responding with a 302 redirect. The actual content of the response is visible is clear text. Note that this capture is at the network level.
If this response were sent from the server to the client in an encrypted SSL session, the packet would essentially be the same except that the 302 response data would be hashed. Only the browser on the client’s machine is capable of decrypting the hash and reading the data.
It is important to note that the secure SSL tunnel is between the client browser application and the web server application.
Forefront TMG is capable of scanning traffic flowing through it for malware, but when the conversation happens over an encrypted SSL tunnel, Forefront TMG cannot perform any layer 7 deep packet inspection. A download that contains a piece of malware will pass straight through Forefront TMG if the communication is encrypted with HTTPS. Fortunately, Forefront TMG has a way around this via its HTTPS Inspection feature.
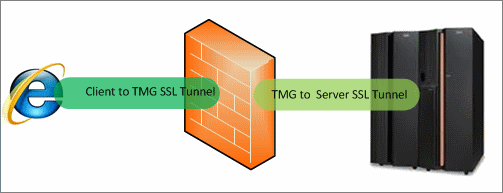
How HTTPS Inspection Works
When HTTPS inspection is enabled in Forefront TMG, the single secure tunnel between the client browser and the web server is split in two. Forefront TMG becomes the tunnel termination point, establishing a secure tunnel with the web server. This enables it to decrypt and inspect the data coming from the web server. To keep everything secure, Forefront TMG establishes a second tunnel from itself to the client machine.
HTTPS Concerns and Misconceptions
Privacy
Because the Forefront TMG server effectively breaks the trusted secure connection between the client and the web server, it introduces privacy concerns. These can be a prohibiting factor that limits the use of HTTPS inspection due to law or policy.
Blocking Secure Sites
One common misconception is that HTTPS inspection needs to be enabled in order to block secure sites. URL filtering and access rules work on the unencrypted 'control data', and are therefore unaffected by HTTPS inspection. See Blocking Sites with Forefront TMG.
Reporting
Web sites listed in Forefront TMG's Reports, as well as the reports in Fastvue TMG Reporter are also unaffected by HTTPS inspection. These reports are built from log data that includes the full URL of the site, not the site's content. Details such as the client IP, authenticated username, access rules and site name remain the same regardless of the conversation being encrypted or not.
Reporting on HTTPS Traffic
It is useful to report on your organization's HTTPS traffic to get an idea of the HTTPS risk profile, especially if you are trying to make the decision about whether or not to enable HTTPS Inspection.
The easiest way to report purely on HTTPS traffic is using Fastvue TMG Reporter 2.1 (currently in Beta, download here). The new filtering feature allows you to filter your reports by Protocol Equal to SSL-tunnel. It is important to specify SSL-tunnel (as opposed to HTTPS) as this is the way the HTTPS protocol is recorded in TMG's Web Proxy Logs.
Another option is to filter by Destination Port Equal to 443
Here is a screenshot of the new Activity Report in TMG Reporter 2.1 when filtered by Destination Port Equal to 443.
TMG Reporter's Activity and Overview reports will show you the sites, categories and productivity ratings of SSL sites, as well as the percentage being blocked/allowed, and the current policy rules in play. This helps you identify and quantify the potential risk associated with SSL tunnels, providing justification to enable the added security of HTTPS inspection.
Separate Access Rules for HTTPS traffic
If you need fine-grain control over HTTPS traffic, a good idea is to create separate Forefront TMG web access rules for HTTPS. To do this:
- Open the Forefront TMG Management Console
- Select Web Access Policy
- Locate your rule that allows internet access for users
- Right click copy | Right click paste
- Open the new rule and rename it to indicate HTTP traffic only
- Select the Protocols tab and remove all protocols except HTTP
- Click OK to save the changes.
- Select the original rule
- Rename the rule to indicate HTTPS traffic only
- Select the Protocols tab and remove all protocols except HTTPS
- Click OK to save the changes
- Verify that the access rules are below the URL filtering deny rules.
- Click the Apply Button to apply the changes.
Once some traffic has been filtered through the new rules, you will see the results on TMG Reporter's live dashboard under the Firewall section. You can drill down into these rules to view more details about the traffic, and use this information to customize the rules over time.
You can also see this information in Company Overview or User Overview reports in the Firewall Rules section.
Summary
HTTPS inspection is a very useful feature in Forefront TMG 2010, in order to guard against malware transmitted over an encrypted SSL Tunnel.
HTTPS inspection does not need to be enabled to block sites that use HTTPS (such as facebook.com), nor is it required for reporting on HTTPS (SSL) sites.
To get a more accurate picture of your organization's HTTPS traffic, use Fastvue TMG Reporter 2.1 to run a filtered report by Protocol Equal to SSL-tunnel, or Destination Port Equal to 443.
These reports can help you determine your HTTPS risk profile and justify whether or not you need to enable HTTPS inspection in Forefront TMG.
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Make The World A Better Place with Fastvue and Microsoft Reputation Services (MRS)
How to Report on YouTube Activity with Fastvue TMG Reporter