How To Secure The Fastvue Sophos Reporter Web Site
by

Etienne Liebetrau
By default, Fastvue Sophos Reporter is open and unrestricted for anonymous users to view. For a number of privacy related reasons you might need to restrict access to the site. You may also want to further restrict access to the Settings tab to prevent unauthorised users from making configuration changes to Sophos Reporter. To improve security even further, it is a good idea to add SSL encryption for authentication.
In this article I will show you how to restrict access to the Sophos Reporter website, and further restrict access to the Settings tab using Windows Authentication and Authorization Rules in IIS, and how to enable SSL (HTTPS) for the site.
Restricting User Access
The simplest way of achieving this is by using IIS authorization rules. There a few prerequisites. All of the following needs to be performed on the Fastvue Sophos Reporter server.
Create Groups
- Open Server Manager and browse to Configuration | Local Users and Groups
- Create a group for Fastvue Viewers
- Populate this group with the AD users and groups that need to view Sophos Reporter’s dashboards and reports
- Create a group for Fastvue Admins
- Populate this group with the AD users and groups that need access to the Settings Tab
Configuring IIS
All the following steps will be performed in the IIS Management Console on the Fastvue Sophos Reporter server. Depending on your configuration you may need to install the ‘Windows Authentication’ and ‘URL Authorization’ Role Services for IIS in Server Manager.
Enable Authentication
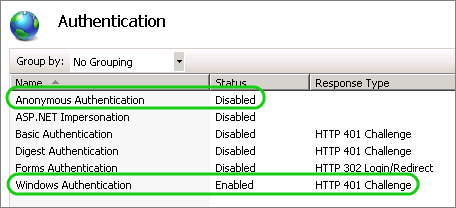
Authorization rules require that users authenticate. We will therefore first enable Windows Authentication.
- Select the Fastvue Sophos Reporter IIS site (in this case it is Default Web Site)
- Select Authentication
- Select and Disable Anonymous Authentication
- Select and Enable Windows Authentication
Allow Access to the Site
- Select the Fastvue Sophos Reporter IIS site again
- Select Authorization Rules
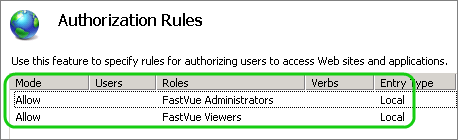
- Select Add an Allow Rule
- In the specified roles or users group, add the Fastvue Viewers group created earlier
- Create another allow rule this time for the Fastvue Administrators
- Remove the Allow all users rule
Remove Access to the Settings Tab
At this point user access to the Fastvue Sophos Reporter site will be limited to the users specified in the groups. To restrict access to the Setting tab do the following in the IIS Management Console:
- Select and Expand the Fastvue Sophos Reporter site
- Select the Settings folder under the Fastvue Sophos Reporter website
- Select Authorization Rules
- The rules created earlier will be inherited here.
- Select and Remove the Fastvue Viewers rule
At this point only the Fastvue Administrators group should have access to the Settings tab. If you are testing this remember to close the browser to end the user sessions.
Securing the site with HTTPS
Any site that requires credentials to be passed should be secured using SSL encryption. This means using HTTPS and certificates. For this article we will be using an internal self-signed certificate but in practice it is better to use a certificate from your internal PKI or a third party CA such as VeriSign.
Generate a Certificate
- Open the IIS Management Console
- Select the IIS server itself (not the site)
- Select Server Certificates
- Select Create Self-Signed Certificate
- Specify a friendly name for the certificate. A good practice is to use the server’s FQDN name. This will generate a certificate that matches the server’s name.
Add the HTTPS Binding
- Select the Fastvue Sophos Reporter IIS website (e.g. Default Web Site on the left)
- Under Actions on the right, select Bindings…
- Select Add
- Change the type to HTTPS
- In the SSL certificate box select the Self-Signed Certificate created earlier
- Click OK to finish the change
Enforce SSL
- Select the Fastvue Sophos Reporter IIS website again on the left
- Select SSL Settings
- Check the Require SSL Box and then Apply on the right hand side
The Fastvue Sophos Reporter site will now require HTTPS and users to be authenticated. At this point you will see a certificate warning since the self-signed certificate is not from a trusted CA on the client machine. Using either an internal PKI or a third party CA certificate would resolve this issue.
Another issue you will notice is that when attempting to connect to the site using HTTP you will get:
403 – Forbidden: Access is denied Error
To fix this, we can change the 403 error page to redirect us to the HTTPS site.
Customize Error Pages
- Still in the IIS Management Console, select the Fastvue Sophos Reporter site on the left
- Select Error Pages
- Select and Edit 403
- Select the Respond with a 302 redirect option
- Specify https:// followed by the FQDN of your site. For example, https://fastvue01.mydomain.com. Make sure you specify the S in https://
Now when you try to access the site via plain http, you will be redirected to the https site instead of seeing the 403 error message.
Change the Fastvue Site Settings to use HTTPS
When Fastvue Sophos Reporter sends an email such as a scheduled report or an alert, it uses the URL set in Settings | Site Settings as the domain in these links back to the application. Now that you've secured the site using HTTPS, it is a good idea to change the Site Settings to also use HTTPS to avoid being redirected to the root of the website by the custom error page configured above.
To edit the Site Settings:
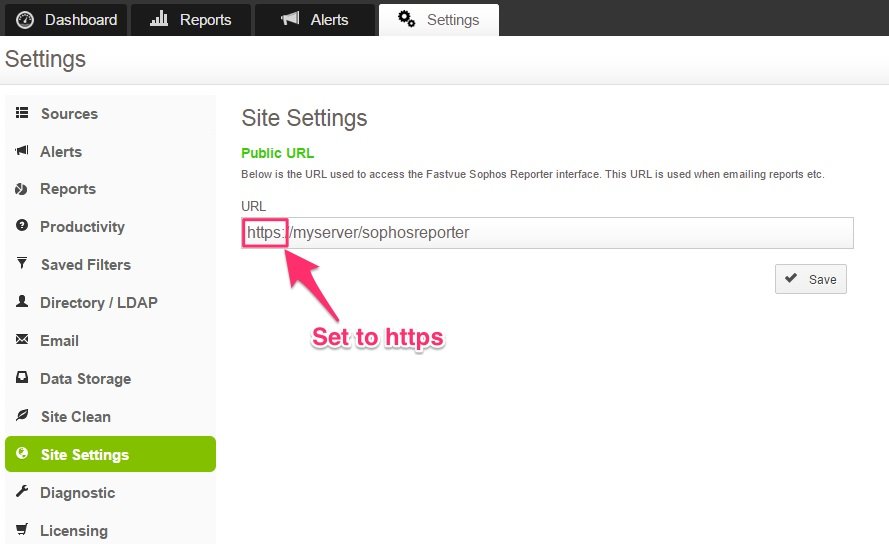
- In Fastvue Sophos Reporter, click the Settings Tab and go to the Site Settings section
- Change the URL to use https:// instead of http://
- Click Save
Summary
If you followed through the steps above, Fastvue Sophos Reporter will now be secured using Windows Authentication. Two user groups can access Sophos Reporter, but only the admin group can access pages on the Settings tab, and the site can only be accessed via HTTPS / SSL.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How To Secure Fastvue Reporter for Private Report Sharing
How To Secure Fastvue TMG Reporter for Private Report Sharing