Optimizing Firewall Logging for Accurate Reporting in Fastvue Reporter

by

Scott Glew
Getting accurate, meaningful web usage reports isn’t just about having the right reporting tool; it also relies heavily on how you configure your firewall. As we've worked alongside thousands of organisations deploying Fastvue Reporter, we've tested and optimised firewall settings to ensure the most insightful, noise-free reporting possible. Here’s our advice on getting it right.
Enable web logging and filtering
Most firewalls have a web content filtering feature, which not only blocks inappropriate, unproductive, illegal, and malicious content but also ensures full URL and website category logging. Even if you’re not actively blocking content, enabling web content filtering allows Fastvue Reporter to provide clear, detailed insights into internet usage.
Generally speaking, this is the process to ensure web content filtering is enabled on your firewall:
Log in to your firewall and look for its web filtering or content filtering feature. This feature may need to be licensed and/or globally enabled.
Configure the feature to allow/block web categories. For example, allow Search Engines, but block Gambling.
Often, you need to configure a firewall policy that uses this web filtering configuration. For example, create a policy for admins with a specific web filtering configuration, and another policy for users with its own web filtering configuration.
Ensure logging is enabled for both allowed and blocked categories. Sometimes firewalls have another action, such as Monitor, which allows and logs the traffic (e.g., Fortinet FortiGate firewalls)
This helps Fastvue Reporter categorise web activity accurately, giving you better visibility into productivity, security risks, and compliance.
Enable user authentication for better insights
If your firewall isn’t identifying users, web activity is logged with IP addresses instead of usernames. This limits the ability to generate reports based on individuals, departments, or security groups.
Generally speaking, this is the process for ensuring your firewall is logging usernames along with traffic:
Log in to your firewall and look for User / Group or Authentication Settings
The two most common user authentication methods include
AD SSO: This usually involves installing an agent on your Active Directory server that tells the firewall which user has which IP address.
Captive Portal: This involves sending the user to a login page before they can access the internet.The Firewall will communicate with your authentication server (LDAP, SAML etc) to verify the credentials.
Radius: This is a common method for identifying users logging in via your wifi system. A Radius server will send Radius packets to your firewall informing it of who has what IP address.
Once your firewall is integrated with an authentication technology, you must then configure policies where users or groups are in the ‘Source’ of the policy, instead of just IPs and network ranges. For example, instead of an outbound web access policy applying to all devices on 192.168.1.0/24, add a group such as ‘All Users’ to the source of the policy.
If possible, monitor the Firewall logs to ensure the ‘Username’ field is now populated with proper usernames.
Once your firewall is logging usernames along with traffic, Fastvue Reporter can match web activity to actual people, making reports much more useful.
Enable Deep Packet Inspection for full URL visibility
With most of the web now using HTTPS, Deep Packet Inspection (DPI) (also called HTTPS Inspection or SSL Decryption) is not only an essential technology for protecting your network from threats transmitted over HTTPS but also for reporting on web usage traffic.
Without DPI, your firewall will only log the domain of a website, such as www.google.com, but you often need to know the full URL such as www.google.com/search?q=fastvue+reporter.
This makes DPI essential for getting visibility into searches, YouTube videos, downloaded files, images, and more.
Fastvue Reporter also utilizes full URLs for its Site Clean algorithm to clean 'Junk' URLs from your reports. For example, we don't want to clean visits to https://www.facebook.com from your reports, but we do want to clean hits to Facebook 'Like' buttons on other pages. Facebook 'Like' buttons come from the URL https://www.facebook.com/plugins/like.php. Without DPI, your firewall will only log www.facebook.com, leaving the Site Clean engine unable to clean the 'like' buttons from your reports.
Deploying DPI Certificates
Unfortunately, enabling DPI isn’t a simple ‘turn it on’ feature and does require some planning. Every device going through a policy with DPI enabled must trust the same ‘certificate’ that the firewall is using to decrypt HTTPS traffic. This means you need to install a certificate on every device, including BYOD devices, in order to apply DPI . This is easily achieved with managed or domain-joined devices, but BYOD devices may require some thought. Some options include:
Onboarding solutions that can deploy certificates during network access (e.g. SecureW2 or Packetfence),
Email the certificate to users with installation instructions
Host an internal web page where users can download and install the certificate before joining your network.
Once the certificate is deployed and trusted by your devices, you can enable DPI on your firewall.
DPI exclusions for trusted apps
The other issue administrators face with DPI is around some non-browser applications breaking. Background applications that require internet access, such as Dropbox, Google Drive, Loom, etc, may stop working when going through a policy with DPI enabled, as they have a copy of their own certificate ‘embedded’ in the app - a practice called ‘certificate pinning’. When they connect to their servers and your firewall intercepts the traffic and signs it with its own certificate, the app will reject the connection.
To get around this, you need to add exceptions to your DPI policy, but be wary of adding exceptions such as *.google.com, as now everything on the Google domain, including searches on www.google.com will no longer be decrypted and logged. Google specifically publishes a list of more specific exceptions here.
There’s usually a day or two of pain, adding exceptions and incrementally rolling out DPI to more users, but once configured, your network will be much more secure, and you’ll have visibility into what you need to keep it secure.
Enable name resolution for IP-based traffic
Even if user authentication is enabled, some types of traffic, such as Servers, Windows and anti-virus updates, guest networks, and BYOD devices, may be excluded.
In these cases, Fastvue Reporter will attempt to resolve IP addresses to hostnames, but if you can have your firewall log resolved IPs directly, then this reduces unnecessary lookups by your Fastvue server.
Some firewalls resolve and log hostnames automatically with nothing to configure, but others require you to enable this feature. For example, in SonicWall, go to Log > Name Resolution, and in FortiGate, ensure ‘Device Detection’ is enabled on the interface.
This helps ensure that unidentified traffic appears as meaningful hostnames in reports rather than raw IP addresses.
Enable referrer URL logging
One of the key components of Fastvue’s Site Clean engine is referrer URL logging. When enabled, this allows Fastvue Reporter to identify actual websites visited and filter out background connections, ad trackers, and embedded content.
Many firewalls log referrer URLs by default, but the following firewalls need to have referrer URL logging explicitly enabled:
Palo Alto Networks - Log Referrer URLs with HTTP Header Logging
Fortinet FortiGate - Configure logging of all URLs and Referrer URLs
Once enabled, your firewall will log referrer URLs for HTTP requests and HTTPS requests if DPI is enabled (see above), and Fastvue Reporter will more accurately show the intentionally visited websites in reports.
Block the QUIC Protocol for Better Logging
Google, owning many web properties as well as a popular web browser with Chrome (currently used by 60% of the population), introduced QUIC (Quick UDP Internet Connections) to improve web performance. QUIC operates over UDP instead of TCP, reducing connection times and enhancing data transmission efficiency.
While beneficial for user experience, QUIC can bypass traditional firewall inspection, impacting the accuracy of logging and reporting. Initially, this primarily affected Google services like YouTube, Google Search, and Gmail, but QUIC adoption has expanded significantly. Major platforms, including Facebook, Instagram, and many websites now using HTTP/3, rely on QUIC, making it a growing challenge for network monitoring.
Without QUIC disabled, deep packet inspection may only work intermittently, resulting in traffic bypassing security features, gaps in logging, and missing data in reports.
How to Block QUIC on Your Firewall
There are two common ways to block QUIC on modern firewalls.
Use Application Control (or an equivalent feature) to block QUIC traffic.
Create a firewall rule to block UDP traffic on port 443.
Here are some firewall-specific guides:
How to disable QUIC in Google Chrome
You can also disable QUIC directly in Google Chrome if needed for testing:
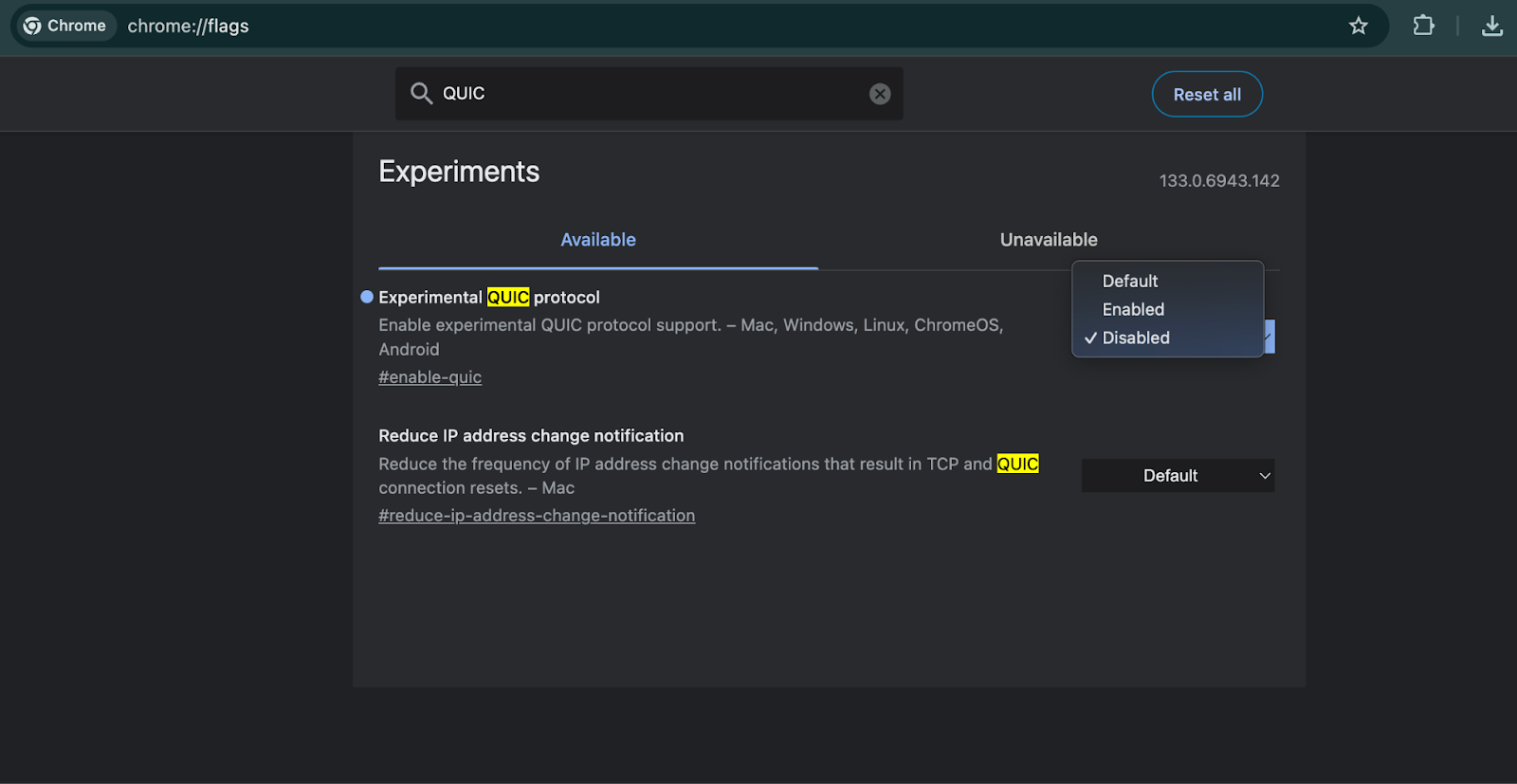
Type
chrome://flagsin the address bar.Find Experimental QUIC Protocol and set it to Disabled.
With QUIC blocked, browsers will fall back to standard HTTPS, ensuring your firewall logs and categorizes traffic accurately across all web services, not just Google.
Check our Getting Started Guides
There may be other firewall-specific options required to get the most detailed logging possible, such as disabling CFS Fastscan in SonicWall, using the IBM LEEF syslog format in WatchGuard, or ensuring all Allowed Web Categories are set to Monitor in Fortinet FortiGate.
Please check our Getting Started for your specific firewall.
Barracuda: Getting Started with Fastvue Reporter for Barracuda
Cisco Firepower (aka Secure Firewall): Getting Started with Fastvue Reporter for Cisco Firepower
Cisco Umbrella SIG: Getting Started with Fastvue Reporter for Cisco Umbrella SIG
ContentKeeper Getting Started with Fastvue Reporter for ContentKeeper
Fortinet FortiGate: Getting Started with Fastvue Reporter for FortiGate
Palo Alto Networks: Getting Started with Fastvue Reporter for Palo Alto Networks
SonicWall: Getting Started with Fastvue Reporter for SonicWall
Sophos Firewall: Getting Started with Fastvue Reporter for Sophos Firewall
WatchGuard: Getting Started with Fastvue Reporter for WatchGuard
Optimise Your Firewall for the Best Fastvue Experience
Configuring your firewall properly ensures that Fastvue Reporter delivers clean, accurate, and actionable reports. By enabling features as user authentication, deep packet inspection, and referrer URL logging, you’ll get:
More accurate user tracking (not just IP addresses).
Full URL visibility, even for HTTPS traffic.
Better categorisation of web activity.
Cleaner reports, free from ad tracking and background scripts.
Still Struggling? Let Us Help
Configuring your firewall for optimal reporting can be tricky, but you don’t have to go it alone. Our support team is here to help you navigate the settings, clear up any confusion, and ensure that Fastvue Reporter gives you the insights you need without the noise.
Have another question?
Got another question? We're here to help. Visit our support section for more information.
- Share this storyfacebooktwitterlinkedIn

