Reporter for FortiGate
Installation guide
Fastvue Reporter can be up and running in as little as five minutes following this simple installation guide.
Minimum Server Requirements
Download Fastvue Reporter and install on a machine (or virtual machine) that meets our recommended requirements below.
Installation
Note: Fastvue Reporter is a resource intensive application by design in order to import data and run reports as fast as possible. We do not recommend installing Fastvue Reporter on a server that provides a critical network service such as a Domain Controller, DNS server, or DFS server. We recommend installing on a dedicated VM (virtual machine) so you can scale the resources appropriately.
To install Fastvue Reporter:
Double-click the downloaded setup exe on a machine that meets the above requirements.
The installer automatically installs and configures the required pre-requisites which include .Net 4.6 and IIS (Web Server and Application Server roles). It will also install Open JDK and Elasticsearch in its own self-managed directory.
Once the pre-requisites have been installed, proceed through the installation wizard. It will ask you for:
Installation folder Only application files are installed to this folder and it does not require much disk space. The default is C:\Program Files\Fastvue\{Product Name}.
Website and Virtual Directory This is the website and sub-folder (virtual directory) within IIS to install the Fastvue Reporter website into. The default is Default Web Site. If you have other websites installed on your server, it is a good idea to either create a new website in IIS first and install to that, or use the 'sub-directory' option and enter a name such as ‘fastvue’ or ‘reports’. This creates a contained 'virtual directory' in IIS under the main website which you can access using http://yourserver/fastvue (for example).
Data Location This is the location where all imported data, configuration and report files are stored. Specify a location with plenty of disk space. The default is C:\ProgramData\Fastvue\{Product Name}.
Upgrading
To upgrade an earlier version of Fastvue Reporter, simply run the new installer over the top of your existing installation. The installer will pick up your existing settings, so just click next throughout the wizard without making any changes. Once installed, browse to the site and clear the browser cache by hitting ctrl + F5 (cmd + R on Mac).
Note that it can take a few minutes for data to start importing again after upgrades and restarts of the Fastvue Reporter service. You can check the database initialisation progress in Settings | Diagnostic | Database.
Automated / Silent Deployment
If you need to deploy or upgrade Fastvue Reporter to silently or to multiple servers in an automated way, please see our comprehensive Reporter 4.0 PowerShell script.
Send syslog data to the Fastvue Server from Fortinet FortiGate or FortiAnalyzer
Now that Fastvue Reporter for FortiGate has been installed, you need to add configure your FortiGate(s) to send syslog data to the Fastvue server.
Alternatively, if you are using FortiAnalyzer, you can forward the FortiGate logs from FortiAnalyzer to your Fastvue Server.
Configure forward, local and anomaly traffic logging
These logging features should be enabled by default, but make sure forward and local traffic as well as anomalies are being logged with the following CLI commands:
config log syslogd filter
set forward-traffic enable
set local-traffic enable
set anomaly enable
set severity information
endConfigure logging of all urls and referrer urls
The logging of referrer URLs was introduced in FortiOS 5.4, which is a great feature for Internet usage analysis, and FortiOS 6.0 introduced ‘extended logging’ that adds useful HTTP headers to the logs. Unfortunately, you need to enable these features per web filter profile. This is also done at the CLI:
config webfilter profile
edit {name-of-profile}
set web-content-log enable
set extended-log enable
set web-extended-all-action-log enable
-- repeat for all web filter profiles --
endIf you are using proxy-based web filter profiles, also enable the additional web-filter-referer-log option (this option is not required or available for flow-based profiles):
config webfilter profile
edit {name-of-profile}
set web-filter-referer-log enable
-- repeat for all proxy-based web filter profiles --
endChange Allowed Web Filter Categories to Monitor
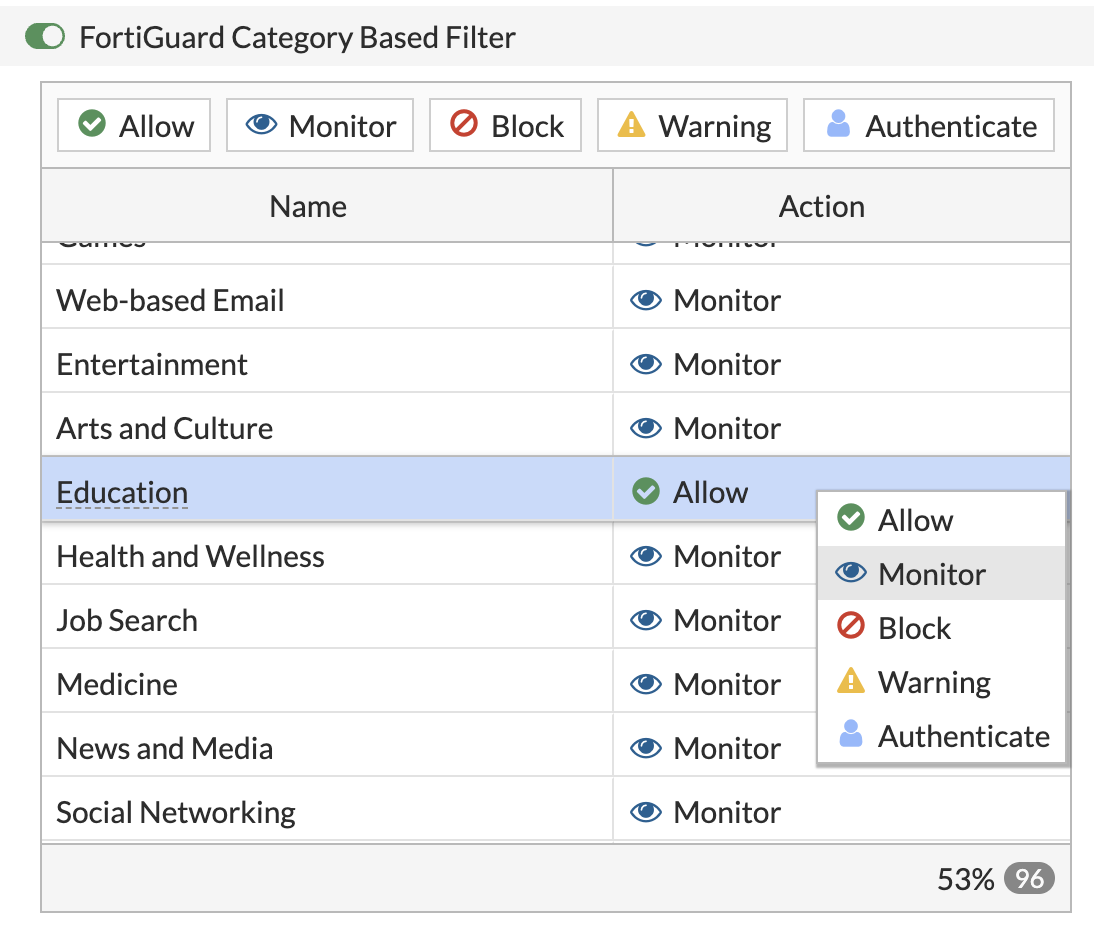
In order for FortiGate to log the details of allowed web traffic, you need to change any web categories from Allow to the Monitor action in your Web Filter Profiles.
To do this:
In FortiGate's Web UI, go to Security Profiles > Web Filter
Under the FortiGuard Category Based Filter section, select all web filter categories currently set to Allow. Hold shift or control / cmd to select multiple categories at once.
Change the action to Monitor by clicking the Monitor action button at the top of the table, or by right-clicking and selecting Monitor.
![FortiGuard Category Based Filter - Change allow to monitor FortiGuard Category Based Filter - Change allow to monitor]()
Save the changes and repeat for any other Web Filter Profiles in use.
Add a Source
Add your firewall as a Source in Fastvue Reporter. This can be done on the start page that is presented after installation, or by going to Settings | Sources and clicking Add Source.
If your firewall is sending syslog data on port 514, click into the dropdown and wait a few seconds. The dropdown will populate with the name and/or IP of the device(s) sending syslog traffic to the Fastvue Server. Simply select your firewall from the list and click Add Source.
If your firewall is sending syslog data on a different port (such as 50514 if using the Linux / Docker version), Fastvue Reporter will not automatically display your firewall in the dropdown list. In this case, manually enter your firewall's IP and your selected syslog port into the options provided, then click Add Source.
Note: If entering your firewall and port manually, make sure the IP is the one your Fastvue Server is receiving syslog data from. This could be the IP of the internal LAN interface on your firewall, or if you have intermediate devices routing syslog traffic, it could be the interface IP of the last hop.
If you're unsure, you can a 'dummy' source with an invalid name (such as 'dummy') but specify the custom syslog port your firewall is sending syslog data on. Fastvue Reporter will then start listening on the port specified. You can then click Add Source again, and the dropdown list should populate with any device sending syslog data on your custom syslog port.
It may take 10-20 seconds before the first records are imported. You can watch the records and dates imported in Settings | Sources. Once records start importing, you can go to the Dashboard tab to see your network traffic.
Enjoy
Now you can try out the many features of Fastvue Reporter!