Sophos SG and Amazon VPC VPN Setup and Testing Guide
by

Etienne Liebetrau
This guide steps through configuring and connecting a Sophos SG to an Amazon Virtual Private Cloud (Amazon VPC) via Site-to-Site VPN.
Throughout this guide, I will refer to the 192.168.x.x network and subnets I used. This is for illustrative purposes only, you are free to use your own address space.
Configuring an Amazon VPC template
We are going to use the wizard with one of the templates to build out a simple VPC network that supports VPN connectivity. This will provide all the required VPC components for us including subnets, route tables, network ACLs etc.
- Click VPC Dashboard to get to the VPC landing page
- Click Start VPC Wizard
- Select VPC with public and private subnets and hardware VPN access
- Specify your VPC supernet (192.168.128.0/22)
- Specify a Name
- Specify the public subnet address (192.168.128.0/24)
- Specify the private subnet address (192.168.129.0/24) and click Next
- Specify the SG's Public IP address *
On the VPC gateway configuration screen provide the following details.
- Specify a Gateway Name
- Specify a VPN Connection name
- Routing Type Dynamic (Requires BGP) **
- Create VPC
The VPC will take a few minutes to create. You will need the configuration file that is generated at the end of the process to proceed.
Note * The public IP address can be behind a NAT (In my case the SG is behind my internet router with a 192.168.0.x IP address on the WAN interface)
Note ** BGP is required but don't be too alarmed. You do not need to configure anything manually and in this case, BGP only applies to the VPC subnets.
Configure Sophos SG for Amazon VPC connectivity
To connect Sophos SG to the Amazon VPC we can make use of the configuration import feature for Amazon VPC. This greatly simplifies the process of setting up the connection. In the AWS console:
- Select VPC Service | VPN Connections
- Choose the VPN Connection we created with the VPC
- Click the Download Configuration button and Save the file
The following steps need to be performed on the Sophos SG:
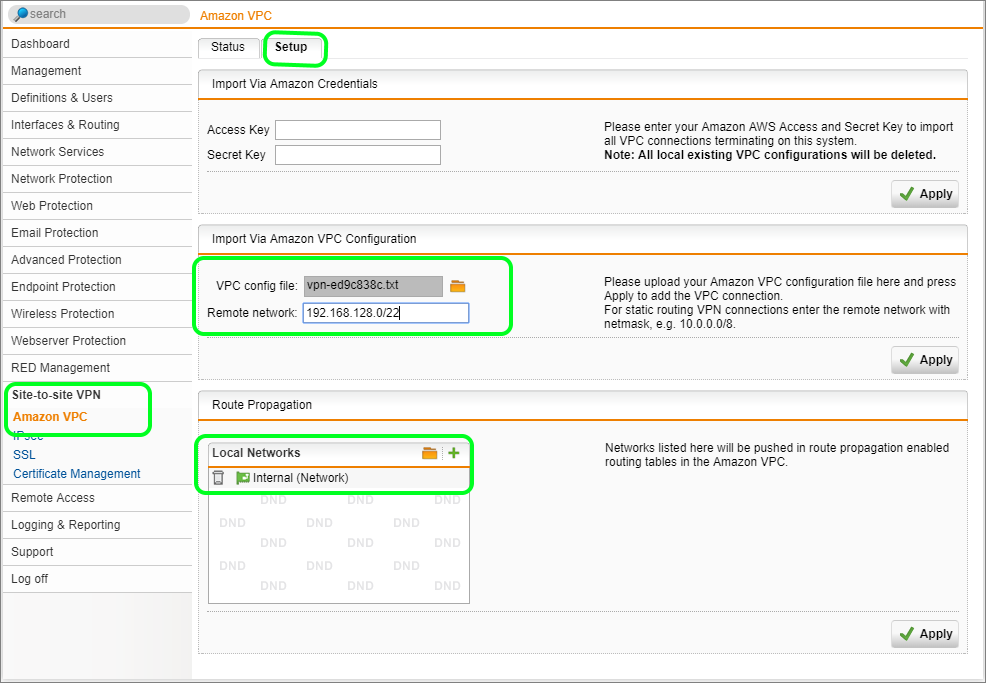
- Log onto the SG and navigate to Site-to-site VPN | Amazon VPC | Setup
- Upload the VPC configuration file
- Specify the entire VPC network range (192.168.128.0/22), and click Apply
- For Route Propagation remove any entry and only specify the relevant local network (192.168.2.0/24), and click Apply
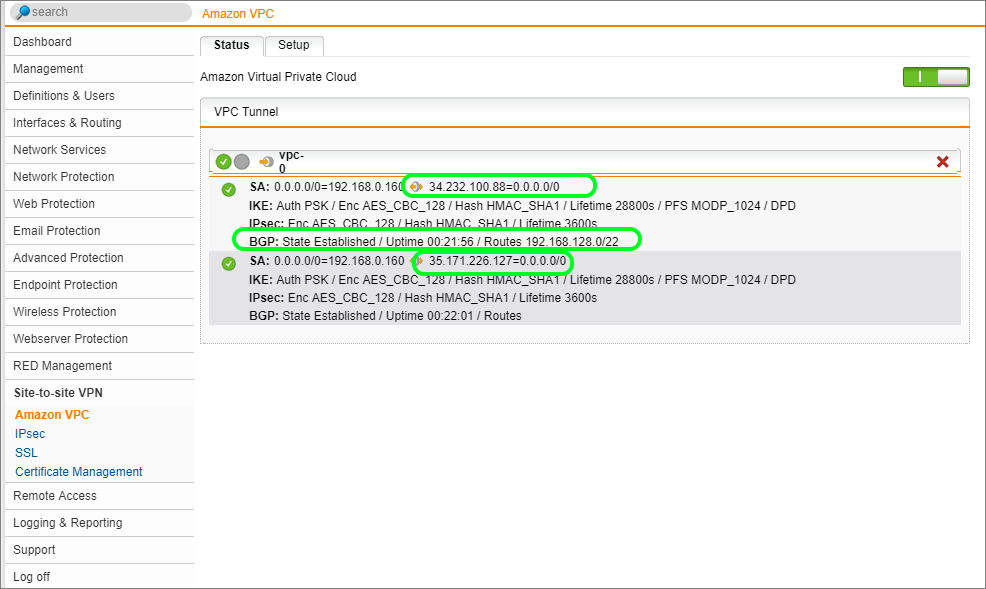
To enable the connection, select the Status tab and switch the toggle to on.
Wait to see if the tunnel connects, which can take 2-3 minutes. You can check the VPN log to see what actions are happening in the background. Should the connection fail this would be the first place to start looking for errors.
There is quite a bit of information on this screen. Please note that there are two connections to two different AWS public IP addresses. Both connections are establishing from our single IP address (192.168.0.160). Only the top tunnel is active and has the route for the VPC associated with it. Should the top tunnel fail the route will move to the second tunnel.
Did you know: Fastvue Sophos Reporter produces clean, simple, web usage reports using log data from your Sophos UTM that you can confidently send to department managers and HR team.
Configure Sophos SG to Amazon VPC access rules
At this stage, you have a tunnel configured to the VPC network and by default, the AWS Network ACLS will allow all in and outbound traffic. The Sophos SG, on the other hand, will need to have some firewall rules added.
- On the Sophos SG management console Select Network Protection | Firewall, and create a new rule
- For Sources specify the LAN (192.168.2.0/24)
- Services can be any (for now)
- Destination - create and add a new network called VPC-Private-Subnet (192.168.129.0/24)
- Action Allow
- In Advanced settings Check Log Traffic and click Save
To allow traffic originating from the VPC to connect the local network you can simply clone this rule and reverse the Sources and Destinations fields.
Testing Sophos SG to Amazon VPC VPN tunnel connectivity
The easiest way to establish if things are working is to deploy a device instance in your VPC. I did not have much success trying with ICMP pings and traceroutes. You can use any AMI that you are familiar with. The important part is the network configuration.
- Start the EC2 launch Instance wizard
- Specify the relevant VPC
- Specify the Private Subnet of the VPC
- DO NOT auto assign a public IP
- Continue with the rest of the instance wizard and finish
- Once the instance is up and running check what the internal IP address is. Establish an SSH or RDP session to this IP address.
From a device, on your LAN you should now be able to connect to the Amazon VPC private IP addresses through the VPN tunnels. From the AWS instance, you would also be able to access devices back on your local LAN depending on the route propagation and access rules defined on the Sophos SG.
Sophos SG and Amazon VPC VPN security considerations
Keep in mind that the default AWS Security groups are restricted to only the required access. You can now choose if you want to use either AWS security groups, AWS network ACLS, or Sophos SG firewall rules to control access between the two networks. A good practice would be to use both. But in a complementary manner, rather than simply duplicating the configuration on both platforms. AWS makes it very easy to configure VPN tunnels between the VPC and the on-premises network. The AWS client and cloud "shared security responsibility" model still applies when it comes to what you allow or deny through the VPN tunnels.
Take the pain out of reporting on Web Usage and Network Traffic.
Now that your Sophos SG to Amazon VPC VPN is configured, why not make your life easier and setup Fastvue Sophos Reporter? Fastvue Sophos Reporter consumes syslog data from Sophos UTM (SG) and Sophos XG Firewalls and produces clean, simple, web usage reports that you can confidently send to department managers and HR team. Automate reports and get the job of reporting on web usage off your desk and into the hands of people that need it. Download the 30 day free trial today!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Configuring a Site-to-Site VPN Between Sophos UTM (SG) and Sophos XG
A Simple Guide To Deploying A Site To Site VPN Using Sophos UTMs