Network Troubleshooting with Sophos UTM tcpdump Packet Captures
by

Etienne Liebetrau
Sophos UTM (SG), like almost all Linux based systems, has the native functionality to perform a tcpdump to capture and show network packet information. This information is very useful in troubleshooting connectivity issues as they show every packet that the firewall has to handle.
The Sophos UTM tcpdump utility that makes this possible is not accessible from the web-UI. You need to connect to a remote shell using an SSH client like putty.
In this article, I will show you how to configure shell access to Sophos UTM and use the tcpdump command to verify if syslog packets are leaving your Sophos UTM appliance. This can be useful when troubleshooting if no log data is showing up on your Fastvue Sophos Reporter server (if you're experiencing this issue, please see our support article on the full list of troubleshooting steps).
Configuring Shell Access on Sophos UTM
By default, shell (or SSH) access to your Sophos UTM SG is disabled. To enable shell access:
- Navigate to Management | System Settings | Shell Access
- Toggle the switch to enable access
- Specify and repeat a root password
- Specify and repeat a loginuser password
- Click Set Specified Passwords
- Change allowed networks from Any to Internal (Network). This is optional but strongly recommended!
- Click Apply
Access the Sophos UTM Shell
You can use any SSH client application for shell access, I personally use PUTTY.
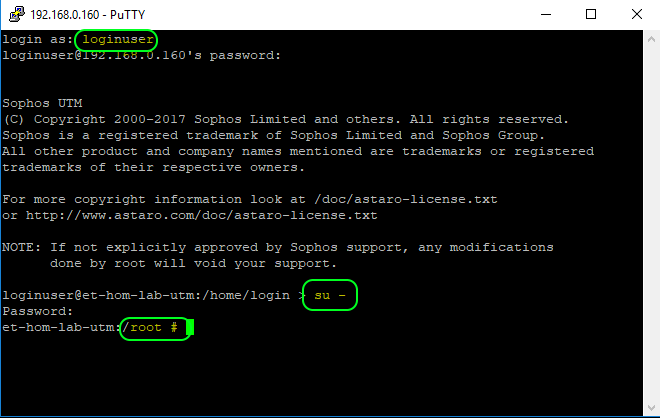
To access the Sophos UTM Shell using Putty:
- Launch Putty and specify the management IP of the Sophos UTM, port 22, and SSH as the connection type
- On first connection, you will be prompted to trust a certificate. Click Yes
- When prompted for a login, enter loginuser
- Specify the password and press enter
- To use tcpdump, you need to elevate your session to root. Do this by entering su-
- Specify the root password
Run the Sophos UTM tcpdump command
The tcpdump command has numerous options to allow you to capture network packets and render them in different modes. The example below will help you identify if your Sophos UTM is actually sending syslog packets to your Fastvue Sophos Reporter server.
tcpdump -i any host 192.168.2.10 and port 514 -nn -XX (Substitute 192.168.2.10 for your own Fastvue server's ip)
Did you know: Fastvue Sophos Reporter produces clean, simple, web usage reports using log data from your Sophos UTM that you can confidently send to department managers and HR team.
The Sophos UTM SG appliance has a remote syslog buffer. This means that syslog messages such as web filtering logs are batched and sent through as opposed to being sent through as they occur. Because of this, you may have to run the tcpdump for a minute or so to actually capture some syslog packets.
When you do capture a syslog packet, it will look similar to the example below.
Examining the Sophos UTM tcpdump Packet Capture
A captured syslog packet with the suggested setting will show the following characteristics
Timestamp Source-IP.Source-port > Destination-IP.Destination-port
The HEX and ASCII section will show the actual content of the packet. Here you should be able to identify enough information to see that this is a web activity log entry.
This verifies that the web filtering syslog messages are correctly being sent from 192.168.2.1 to 192.168.2.10:514. If you're not seeing the syslog data arrive on 192.168.2.10, then there could be another device or a local firewall preventing the packets from being received.
Conclusion
Sophos UTM tcpdump information is very useful in troubleshooting connectivity issues. Unlike log files, the packet capture shows you what is actually happening "on the wire" and will show every packet that the firewall has to handle.
The example above shows how to use tcpdump to verify if syslog packets are leaving your Sophos UTM appliance but the same techniques can be used with other tcpdump commands to troubleshoot other similar issues.
Here are some useful tcpdump resources with commands you may like to familiarise yourself with:
- https://hackertarget.com/tcpdump-examples/
- https://danielmiessler.com/study/tcpdump/
- https://www.tcpdump.org/manpages/tcpdump.1.html
Take the pain out of troubleshooting your Sophos UTM
Packet captures are great, but why not make troubleshooting your Sophos UTM even easier and setup Fastvue Sophos Reporter? Fastvue Sophos Reporter consumes syslog data from Sophos UTM (SG) and Sophos XG Firewalls and produces clean, simple reports to help you troubleshoot bandwidth, web filtering policies and Internet usage productivity issues. You can also automate reports to get the job of reporting on web usage off your desk and into the hands of people that need it. Download the 30 day free trial today!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Filtering and Forwarding Sophos UTM Syslog Data with Syslog-ng
How To Allow Skype Through Sophos UTM in Standard Proxy Mode