Reporter for FortiGate
Installation guide
Fastvue Reporter can be up and running in as little as five minutes following this simple installation guide.
Fastvue Reporter can be deployed on Linux operating systems using Docker.
What is Docker?
Docker is a popular open platform that makes it easier to create, deploy, and run applications by using containers. Containers are lightweight and contain everything needed to run the application, so you do not need to rely on what is currently installed on the host.
For more information see https://docs.docker.com/get-started/overview/.
Why Fastvue Reporter uses Docker
Running Fastvue Reporter on Linux requires a range of pre-requisites and specific versions of those pre-requisites. Instead of managing them directly on the host, all you need to worry about is installing Docker, and using our pre-built Docker images to deploy a Container. This container has all the pre-requisites Fastvue Reporter requires and does not affect or conflict with anything you may already have installed on the host.
Getting started
The instructions below take you through loading and running a Fastvue Reporter Docker image as a container, and updating an existing container using a new image.
Deploying a new Fastvue Reporter container
The first step in deploying a new Fastvue Reporter container is to spin up a Linux-based host. We recommend Ubunto.
Configure your Linux Host
Make sure your Linux host meets our recommended requirements:
Install Open SSH
Ensure you can log in to your remote Linux server by installing Open SSH. For example, in Ubuntu:
sudo apt-get install openssh-server
sudo systemctl enable ssh
sudo systemctl start sshTest by logging into the system using
ssh user@server-name
# e.g.
# ssh [email protected]Install Docker
Install Docker on your Linux distro of choice. Please refer to Docker's docs for installations instructions: https://docs.docker.com/engine/install/
⚠️ Note: Some Linux distributions such as Ubuntu provide an option to install the Docker package as part of Ubuntu install. Do NOT do this. This installs the 'snap' version of Docker which does not work for Fastvue Reporter's requirements.
Once installed, enable Docker to run at startup using the command:
sudo systemctl enable dockerInstall Docker Compose
Once Docker is installed, you now need to install Docker Compose following the instructions here: https://docs.docker.com/compose/install/
Load the Fastvue Reporter Docker image
Once you have downloaded the Fastvue Reporter Docker image, you need to copy it to the Linux host and load the image in Docker.
Note: The words
firewall-xyzand{product-name}in the commands and examples below should be replaced with your Fastvue Reporter's product/brand name.
Copy image to host
Copy the downloaded Docker image to your Linux host using scp.
scp <image-filename> user@ip:~
# e.g.
# scp fastvue-reporter-for-firewall-xyz.img [email protected]:~Load the image
ℹ️ The following commands need to be run as root. Switch to root with
sudo suor addsudobefore all commands.
Load the Docker image using:
docker load -i {image-filename}
# e.g.
# docker load -i fastvue-reporter-for-firewall-xyz.img
# cc967c529ced: Loading layer 65.57MB/65.57MB
# ...
# 27f89d75f52e: Loading layer 76.31MB/76.31MB
# Loaded image: fastvue/reporter-for-firewall-xyz:latestList your images with docker image ls to confirm that it was imported;
docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
fastvue/reporter-for-firewall-xyz latest 4328c7039e09 2 months ago 1.19 GBPrepare a data location on the host
Next, create a folder on your machine where Fastvue Reporter's settings and data will be stored. Firewalls can generate a lot of data, so make sure you supply a location with plenty of disk space.
We recommend using /opt/fastvue/reporter-for-{product-name}. Do not use spaces, and don't store it anywhere under /home.
Create the data location using
mkdir -p /opt/fastvue/reporter-for-firewall-xyzIf you happen to be doing this on a Mac, create a folder such as
/Users/<your user profile>/Documents/Fastvue/reporter-for-firewall-xyz
Deploy the container
There are two ways to deploy the Docker container. Using Docker Compose (recommended) or Docker Run
We recommend using the Docker Compose method above as the configuration of your container is saved in a docker-compose file making it easy to update and re-deploy your container in the future when updated images are released.
Using docker compose (recommended)
First, create a directory to contain your docker-compose file. The name of this directory will be used as the name of the Docker stack that gets created when you run docker-compose so give it a meaningful name, such as fastvue-reporter-for-firewall-xyz.
mkdir fastvue-reporter-for-firewall-xyzInside the directory you created, create a file named docker-compose.yml
cd fastvue-reporter-for-firewall-xyz
nano docker-compose.ymlWithin nano, paste in the following contents:
version: "3.3"
services:
fastvue-reporter:
container_name: "fastvue-reporter-for-firewall-xyz"
image: "fastvue/reporter-for-firewall-xyz:latest"
ports:
- "8080:80"
- "8443:443"
- "50514:50514/udp"
- "50514:50514/tcp"
volumes:
- /opt/fastvue/reporter-for-firewall-xyz:/data
- /etc/timezone:/etc/timezone:ro
- /etc/localtime:/etc/localtime:ro
restart: alwaysThe image should be the name of the loaded image in Docker, not the name of the docker image file you downloaded from the Fastvue website.
Also ensure /opt/fastvue/reporter-for-firewall-xyz matches the data location you created above.
Definitions:
container_name: "fastvue-reporter-for-firewall-xyz" Aname to identify the Docker container.image: "fastvue/reporter-for-firewall-xyz:latest" The name of the loaded image in Docker. This is not the name of the Docker image file you downloaded from the Fastvue website.8080:80Map port 8080 on the host to port 80 (HTTP) inside the container.8443:443Map port 8443 on the host to port 443 (HTTPS) inside the container.50514:50514/udpMap port 50514 (UDP) on the host to port 50514 inside the container. This is used for receiving syslog messages./opt/fastvue/reporter-for-firewall-xyz:/dataMap the path/opt/fastvue/reporter-for-firewall-xyzon the host to/datainside the container./etc/timezone:/etc/timezone:ro /etc/localtime:/etc/localtime:roSet the timezone in the Container to the same timezone as the Linux host.
Note: The following two lines map the Docker container's timezone to the Linux host's timezone. This only works on Linux hosts.
- /etc/timezone:/etc/timezone:ro
- /etc/localtime:/etc/localtime:roIf you want to specify the timezone of the Docker container explicitly, or you are using Docker on Windows or MacOS, remove these two lines and replace them with
environment:
- TZ=Australia/PerthReplace Australia/Perth with the appropriate timezone from the TZ Database name column from this page: https://en.wikipedia.org/wiki/List_of_tz_database_time_zones
Write Out the file and press Enter, then exit nano with Ctrl-x.
You can now deploy the container using the following command.
docker-compose up -dThe parameters have the following meanings:
upInstructs docker-compose to deploy the container stack.-dDo not attach the active terminal to the container. This will cause the container to run in the background rather than taking over and being controlled by the terminal you ran thedocker-composecommand from. If this is not specified, you can pressCtrl-Zto detach from the container once it is running.
Using docker run
You can also deploy and run the image directly using the docker run command, specifying all the configuration options as parameters.
Deploy by mapping the Containers timezone to the host's timezone:
docker run -d \
-p 8080:80 \
-p 8443:443 \
-p 50514:50514/udp \
-v /opt/fastvue/reporter-for-firewall-xyz:/data \
-v /etc/timezone:/etc/timezone:ro \
-v /etc/localtime:/etc/localtime:ro \
--restart always \
fastvue/reporter-for-firewall-xyz:latestOr deploy by using the TZ environment variable to set the timezone explicitly:
docker run -d \
-p 8080:80 \
-p 8443:443 \
-p 50514:50514/udp \
-v /opt/fastvue/reporter-for-firewall-xyz:/data \
-e TZ=Australia/Perth \
--restart always \
fastvue/reporter-for-firewall-xyz:latestDefinitions:
--nameA name to identify the Docker container.-dDo not attach the active terminal to the container. This will cause the container to run in the background rather than taking over and being controlled by the terminal you ran thedocker runcommand from.-p 8080:80Map port 8080 on the host to port 80 (HTTP) inside the container.-p 8443:443Map port 8443 on the host to port 443 (HTTPS) inside the container.-p 50514:50514/udpMap port 50514 (UDP) on the host to port 50514 inside the container. This is used for receiving syslog messages.-v /opt/fastvue/reporter-for-firewall-xyz:/dataMap the path/opt/fastvue/reporter-for-firewall-xyzon the host to/datainside the container.-e TZ=Australia/PerthSet the environment variableTZto the provided value inside the container. This will set the timezone for the container. The value specified must be one of the TZ database names at https://en.wikipedia.org/wiki/List_of_tz_database_time_zones-v /etc/timezone:/etc/timezone:ro -v /etc/localtime:/etc/localtime:roSet the timezone in the Container to the same timezone as the Linux host.--restart alwaysThe container will automatically start on host boot, or if the container fails.fastvue/reporter-for-firewall-xyz:latestThe name of the loaded image in Docker. This is not the name of the Docker image file you downloaded from the Fastvue website.
For more docker run parameters and definitions, see https://docs.docker.com/engine/reference/commandline/run/
Check your container is running
You can check your container is running with docker ps
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
75b00d26524b fastvue/reporter-for-firewall-xyz:latest "/bin/bash /opt/fast…" 2 minutes ago Up 2 minutes 514/tcp, 514/udp, 0.0.0.0:50514->50514/udp, :::50514->50514/udp, 0.0.0.0:8080->80/tcp, :::8080->80/tcp, 0.0.0.0:8443->443/tcp, :::8443->443/tcp fastvue-reporter-for-firewall-xyzReset Linux Kernel Connection Tracking
As Docker only creates the iptables rules for forwarding and masquerading incoming traffic to the container once the container is deployed, any existing connection state for the incoming syslog traffic will still be assuming the old rules, which means that your container will likely see the syslog traffic arriving with the source address set to the Docker network's gateway address.
To ensure the container sees syslog traffic arriving from your firewall instead of the Docker network's gateway address, you must reset the Linux kernel's connection tracking.
First install the conntrack tool on your host using your host distro's package manager. For Ubuntu, you can use:
apt install conntrackNow reset the Linux kernel's connection tracking using:
conntrack -FVerify Fastvue Reporter is running
Using a web browser, connect to your host on port 8080 (e.g. http://192.168.1.2:8080 ) and verify that Fastvue Reporter is running.
You can also configure Auth and SSL for the web interface by following the instructions in Apache Config. Changing this configuration does not require redeployment of the container, only a restart.
Configure Authentication and SSL in Apache (optional)
Reporter's Docker image allows for external config files to be included in the container's Apache config to add Auth and SSL configuration that persists between container runs.
These configuration files must exist under the /config/apache path in the mapped data volume.
Inside the container, the mapped data volume exists at /data so any paths that the provided config files refer to must use this as the base directory.
For example, if you store Fastvue Reporter's data at /var/fastvue/reporter-for-firewall-xyz on your host, then on the host the auth config file would be at /var/fastvue/reporter-for-firewall-xyz/config/apache/auth.conf, and the authpasswd file would exist at /var/fastvue/reporter-for-firewall-xyz/config/apache/authpasswd, but inside the container these would exist at /data/config/apache/auth.conf and /data/config/apache/authpasswd.
Configure authentication
Create a Config file in /(basepath)/config/apache/auth.conf
Where (basepath) is the Fastvue Reporter's data path on the host.
Example for Basic auth mode:
AuthType Basic
AuthName "Fastvue Reporter"
AuthUserFile /data/config/apache/authpasswd
Require valid-userThe authpasswd file contains the list of users and their hashed passwords when using Basic auth mode. This file can be created on the host and users added to it using this command.
htpasswd -c (basepath)/config/apache/authpasswd adminWhere (basepath) must be the data location on the host. The -c parameter creates the file, and must be passed only for the first user being added. The final parameter, in the example set to admin, is the username you want to create a password for. The command will ask for a password for the user.
Example for auth using LDAP integration.
AuthType Basic
AuthName "Fastvue Reporter"
AuthBasicProvider ldap
AuthLDAPURL "ldap://dc-server.domain.local:389/DC=domain,DC=local?sAMAccountName?sub?(objectClass=*)"
AuthLDAPBindDN "[email protected]"
AuthLDAPBindPassword "(password)"
Require valid-userThe LDAP URL would be specific to your system configuration, but the ?sAMAccountName?sub?(objectClass=*) part is required. The AuthLDAPBindBN also must either be the FQDN of a user authorised to make auth queries, or the username in UPN syntax (user@domain).
Private Report Sharing
Allowing anonymous or alternate auth access to /_ and /p for private report sharing is supported through a secondary config file named authshared.conf. The directives in this file will only apply to the /_ and /p directories.
Example authshared.conf allowing full anonymous access to /_ and /p regardless of the site root's auth configuration;
Require all grantedIf authshared.conf is not provided, the /_ and /p directories will share the same auth config as the site root, and if the auth.conf file is not provided, the site root will default to Require all granted allowing anybody to access the site.
Configure SSL
Config file at /config/apache/ssl.conf
SSLEngine On
SSLCertificateFile /data/config/apache/sslcert.pem
SSLCertificateKeyFile /data/config/apache/sslprivate.keyThe certificate file sslcert.pem and the key file sslprivate.key can be self-signed or provided separately.
To create a self-signed certificate, the following command can be used;
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout (basepath)/config/apache/sslprivate.key -out (basepath)/config/apache/sslcert.pemWhere (basepath) must be the data location on the host. This command will ask for details for the certificate which the user must enter.
Updating an existing container
When Fastvue releases new updates, you need to update your existing container and image.
Stop and remove the existing container
To do this, first find your container's ID or Name using docker ps and then stop and remove it, using docker stop <container-name> and docker rm <container-name>
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
480948a8931a 67cc5f1b1d11 "/bin/bash/opt/fastvue" 9 days ago Up 4 seconds 514/tcp, 514/udp, 0.0.0.0:50514->50514/udp, 0.0.0.0:8080->80/tcp, 0.0.0.0:8443->443/tcp fastvue-reporter-for-firewall-xyz
docker stop fastvue-reporter-for-firewall-xyz
fastvue-reporter-for-firewall-xyz
docker rm fastvue-reporter-for-firewall-xyz
fastvue-reporter-for-firewall-xyzStop and remove the existing image
Once the container has been removed, find the ID of the existing loaded Docker image using docker image ls, then remove it, using docker image rm <image-id>
docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
fastvue/reporter-for-firewall-xyz latest 27d03835094b 8 days ago 1.25GB
docker image rm 27d03835094b⚠️ If you don't remove your existing image before the next step, docker will rename your old/existing image to an empty string. This can then be removed with
docker image rm <id>
Load and deploy the new image
Once the Docker container and image has been removed, replace your image file with the new one downloaded from the Fastvue website, then follow the steps above load the image and deploy your container.
Send syslog data to the Fastvue Server from Fortinet FortiGate or FortiAnalyzer
Now that Fastvue Reporter for FortiGate has been installed, you need to add configure your FortiGate(s) to send syslog data to the Fastvue server.
Alternatively, if you are using FortiAnalyzer, you can forward the FortiGate logs from FortiAnalyzer to your Fastvue Server.
Configure forward, local and anomaly traffic logging
These logging features should be enabled by default, but make sure forward and local traffic as well as anomalies are being logged with the following CLI commands:
config log syslogd filter
set forward-traffic enable
set local-traffic enable
set anomaly enable
set severity information
endConfigure logging of all urls and referrer urls
The logging of referrer URLs was introduced in FortiOS 5.4, which is a great feature for Internet usage analysis, and FortiOS 6.0 introduced ‘extended logging’ that adds useful HTTP headers to the logs. Unfortunately, you need to enable these features per web filter profile. This is also done at the CLI:
config webfilter profile
edit {name-of-profile}
set web-content-log enable
set extended-log enable
set web-extended-all-action-log enable
-- repeat for all web filter profiles --
endIf you are using proxy-based web filter profiles, also enable the additional web-filter-referer-log option (this option is not required or available for flow-based profiles):
config webfilter profile
edit {name-of-profile}
set web-filter-referer-log enable
-- repeat for all proxy-based web filter profiles --
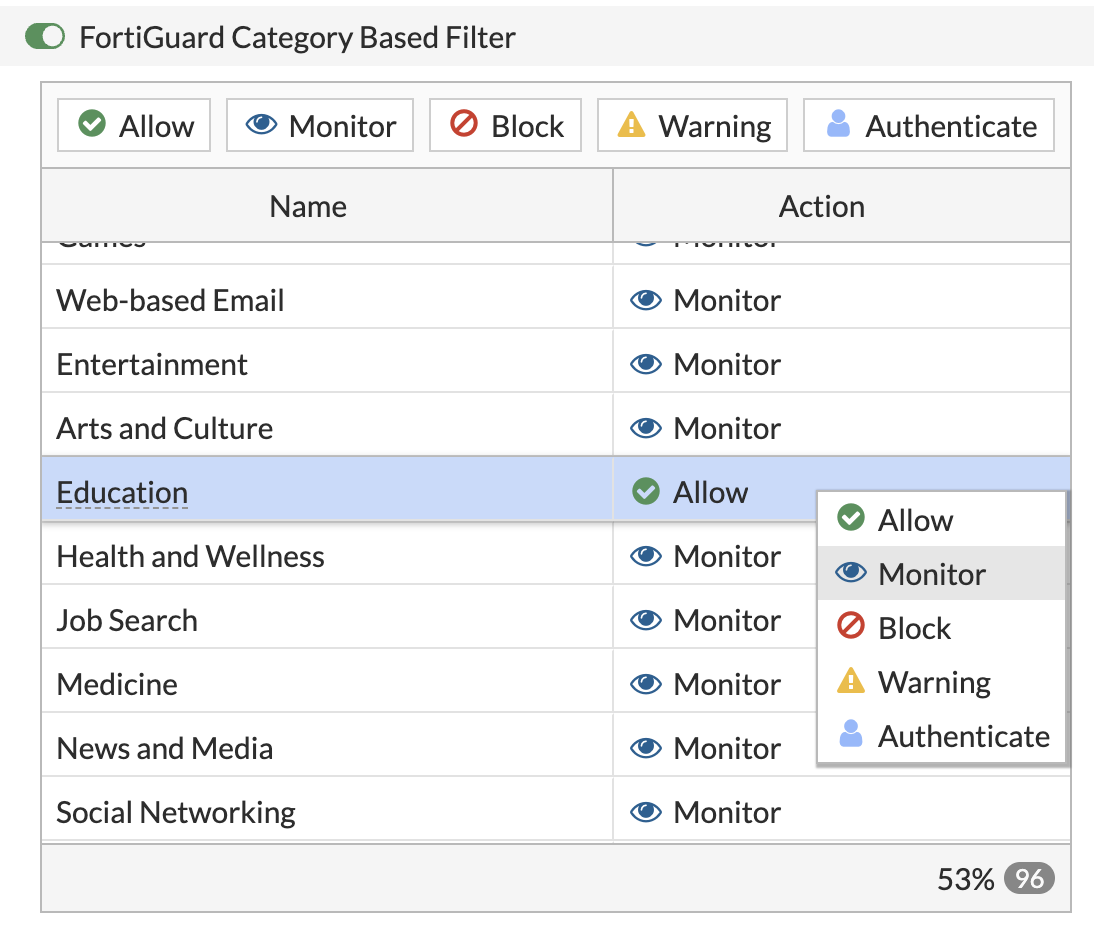
endChange Allowed Web Filter Categories to Monitor
In order for FortiGate to log the details of allowed web traffic, you need to change any web categories from Allow to the Monitor action in your Web Filter Profiles.
To do this:
In FortiGate's Web UI, go to Security Profiles > Web Filter
Under the FortiGuard Category Based Filter section, select all web filter categories currently set to Allow. Hold shift or control / cmd to select multiple categories at once.
Change the action to Monitor by clicking the Monitor action button at the top of the table, or by right-clicking and selecting Monitor.
![FortiGuard Category Based Filter - Change allow to monitor FortiGuard Category Based Filter - Change allow to monitor]()
Save the changes and repeat for any other Web Filter Profiles in use.
Add a Source
Add your firewall as a Source in Fastvue Reporter. This can be done on the start page that is presented after installation, or by going to Settings | Sources and clicking Add Source.
If your firewall is sending syslog data on port 514, click into the dropdown and wait a few seconds. The dropdown will populate with the name and/or IP of the device(s) sending syslog traffic to the Fastvue Server. Simply select your firewall from the list and click Add Source.
If your firewall is sending syslog data on a different port (such as 50514 if using the Linux / Docker version), Fastvue Reporter will not automatically display your firewall in the dropdown list. In this case, manually enter your firewall's IP and your selected syslog port into the options provided, then click Add Source.
Note: If entering your firewall and port manually, make sure the IP is the one your Fastvue Server is receiving syslog data from. This could be the IP of the internal LAN interface on your firewall, or if you have intermediate devices routing syslog traffic, it could be the interface IP of the last hop.
If you're unsure, you can a 'dummy' source with an invalid name (such as 'dummy') but specify the custom syslog port your firewall is sending syslog data on. Fastvue Reporter will then start listening on the port specified. You can then click Add Source again, and the dropdown list should populate with any device sending syslog data on your custom syslog port.
It may take 10-20 seconds before the first records are imported. You can watch the records and dates imported in Settings | Sources. Once records start importing, you can go to the Dashboard tab to see your network traffic.
Enjoy
Now you can try out the many features of Fastvue Reporter!