California K-12 CIPA Compliance: Secure E-Rate Funding with Smart Web Filtering & Monitoring

by

Bec May
CIPA stands for the Children's Internet Protection Act, which was enacted by the US Congress in 2000 to address minors' access to obscene or harmful online content.
These requirements are not simply tick-box measures; actions must be demonstrated and documented, relevant technologies must be implemented, and the public must be consulted.
For E-Rate schools in California, these implementations must also align with state-specific frameworks, including the Student Online Personal Information Protection Act (SOPIPA) and Education Code §49073.1 (AB 1584).
This is no easy feat. When the FCC first issued rules implementing CIPA in 2001, access to the school network was primarily limited to occasional searches on a shared library computer, making the monitoring of student internet use a relatively simple affair.
Fast forward to 2025, and California schools manage 1:1 devices, cloud-based learning platforms, and high-speed networks, all accessible from the classroom to the car park. Students research sensitive topics, message classmates, and stream video content, all on encrypted platforms that can easily bypass legacy filters. It would be a gargantuan task for even a busload of educators to try and visually monitor what's happening on school network-connected devices for a couple of students, let alone an entire K-12 school.
Schools are expected to actively monitor online activity to protect minors from inappropriate content, prevent the disclosure of personal information, and ensure safe online behaviour. The difference now, which is fast becoming a significant challenge for California school districts, is that monitoring can't be left to physical supervision or basic filtering. And for schools that rely on federal E-Rate funding, non-compliance with CIPA isn't just a policy gap; it's a financial risk.
Failure to meet the monitoring and filtering requirements can result in funding losses, audit penalties, and significant reputational damage, especially when student safety and well-being are at stake.
This article breaks down what CIPA compliance actually requires, how those requirements intersect with California's privacy laws, and why schools need to go beyond basic filtering to implement intentional, transparent, and auditable monitoring.
We'll also cover the risks of CIPA non-compliance, the importance of public-facing internet safety policies, and what intelligent school filtering and monitoring look like when done right, particularly for schools that depend on E-Rate program funding.
Quick Reference: California CIPA Compliance Checklist
Here’s what your district needs in place to stay E-Rate eligible under California’s stricter privacy laws.
Before you dive into the details, check where your district stands.
Use this CIPA Compliance Checklist for California Schools to confirm you meet the core requirements for funding eligibility and online safety.
A published and discussed Internet Safety Policy
A working Technology Protection Measure (TPM) or content filter
Active monitoring of student online activity
Documented digital citizenship education program
Clear data privacy and retention policies aligned with California law
Records of public notice and meetings discussing the policy
Evidence of ongoing review and reporting for E-Rate audit readiness
What are the Core CIPA Requirements for California School Districts?
To stay eligible for E-Rate Funding, all US K-12 school districts must comply with the Children's Internet Protection Act (CIPA). CIPA is a federal law, but California school districts have the added complexity of navigating state-level privacy obligations when implementing their internet safety policies.
At its core, CIPA requires:
A formal Internet Safety Policy
CIPA requires K-12 schools to formally adopt and implement an official internet safety policy that must be approved at an open meeting before being implemented in the school system.
The internet safety policy needs to address the following:
Access by minors to inappropriate content on the World Wide Web
The safety of minors using email, chat rooms, and other direct communication platforms
Unauthorised access by minors online via hacking and other unlawful activities
Unauthorised disclosure, use, and dissemination of students' personal information
Measures implemented to restrict minors' access to materials harmful to minors
Monitoring the online activities of minors
Educating minors about appropriate online behavior, including interacting with other individuals on social networking websites and chat rooms, and cyberbullying awareness,
In California, this policy must also satisfy Education Code §49073.1, which requires that any monitoring or data collection performed by third-party tools be clearly defined in contracts and communicated to parents or guardians.
A Technology Protection Measure (TPM)
CIPA requires that schools adopt a technology protection measure, most commonly in the form of a content filtering system, that blocks access to pornography and visual content deemed obscene or otherwise harmful to minors. Basic blocklists aren't enough.
Web Filters need to be:
Continuously active
Effective across encrypted and non-encrypted browsing traffic
Applied to all student-accessible devices on the school network
The school or library is bound to enforce the use of the TPM on internet-connected computers; however, system administrators or an otherwise authorised authority can disable the technology during use by an adult for bona fide research or other lawful purposes.
Monitoring Online Activity
Schools must include the monitoring of students’ online activity in their Internet Safety Policy. In practice, this means schools need real visibility into how students use the internet, what they search, stream, and access, not just whether content is blocked. While CIPA does not mandate any specific monitoring technology, it does require that policies and practices demonstrate appropriate supervision.
Modern internet usage monitoring in K-12 schools means:
Capturing browsing behaviour across HTTPS and search engines
Alerting staff to flagged keyword searches
Creating reports that demonstrate compliance with your school's online safety and security policies. These reports should also satisfy California’s privacy and transparency standards under SOPIPA and AB 1584 by ensuring that any student data used for monitoring remains under district control, is not sold or shared with third parties, and is retained only as long as necessary
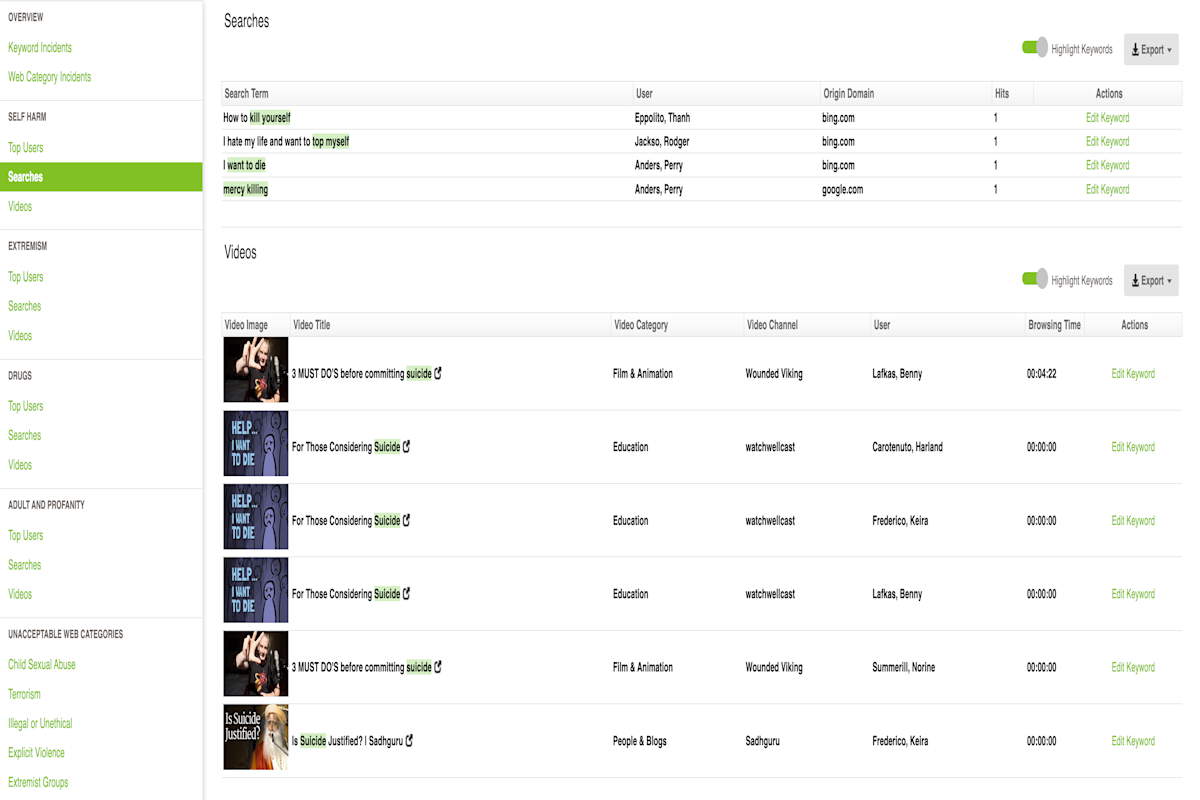
Note: California schools should ensure their filters can inspect encrypted (HTTPS) traffic, as the vast majority of student browsing now occurs over HTTPS. DPI-SSL (or TLS inspection) on supported firewalls such as Fortinet, Palo Alto, Sophos, and WatchGuard enables this visibility when paired with a reporting and analysis solution like Fastvue Reporter, allowing schools to see complete URLs, search queries, and detect keyword triggers such as self-harm or violence, without relying on invasive device-level agents.
Digital Citizenship and online behaviour education
CIPA compliance doesn't just involve policies and technologies for filtering and monitoring online content in schools. It also mandates that schools actively educate students about responsible and appropriate online behaviour. This is often referred to as digital citizenship training, and academic research shows that schools that emphasize digital literacy achieve better outcomes in student awareness and behaviour regarding responsible technology use.
In California, this aligns closely with existing state education standards that emphasise wellbeing, privacy, and online responsibility. Districts can also map this training to the California Department of Education’s Digital Citizenship and Media Literacy Framework, reinforcing that compliance isn’t just about filtering but fostering safe, informed digital participation.
Digital citizenship education should cover:
Safe use of social media and messaging apps
Recognizing and reporting cyberbullying
Educating students on their digital footprint and the potential long-term consequences of online activity (you may want to introduce the three-question rule here, encouraging students to ask themselves the following questions before posting or sending anything online: Would I send this to my grandma? To my teacher? Would I want this to remain online forever?)
Respecting intellectual property and other users' privacy rights
The risks of CIPA Non-Compliance and E-Rate funding loss
For many Californian schools, CIPA compliance isn't just about protecting minors online; it's directly tied to federal funding. The E-Rate program, administered by the FCC and USAC, subsidizes up to 90% of the cost of internet access and network infrastructure for eligible schools. To receive these funds, districts must certify that they have an active Internet Safety Policy, a TPM, and procedures to monitor student online safety. If an audit finds gaps in any of the areas, the financial impact can be severe.
Common consequences of CIPA non-compliance
Loss or clawback of E-Rate funding: The FCC can demand repayment of discounts already issued if schools cannot prove that filtering and monitoring were continuously active during the funding year.
Audit findings and administrative penalties: Inadequate filtering logs, missing policy meeting minutes, or outdated safety policies are red flags that can trigger additional reviews or delay funding renewal. Further, failure to comply with CIPA can result in the loss or clawback of E-Rate funding, delayed renewals, or additional FCC scrutiny.
Legal exposure under state privacy laws: California’s stricter privacy frameworks, including SOPIPA (SB 1177), AB 1584, and the California Consumer Privacy Act (CCPA), mean that a district can be CIPA-compliant but still face penalties if its monitoring practices over-collect or mishandle student data.
Reputational damage and community backlash: Parents and advocacy groups are increasingly aware of digital privacy issues. A single complaint about undisclosed monitoring or data misuse can attract public scrutiny and undermine trust.
How California school districts can align CIPA compliance with state privacy laws
So, we’ve covered the basics of CIPA compliance, but what about state laws?
While filtering and monitoring are central to CIPA, California schools face an added layer of complexity in ensuring that these practices respect student privacy, withstand data requests, and don’t introduce legal risk. That means complying not only with federal requirements but also with stricter state laws on data collection, consent, and transparency.
In practice, this means every keyword alert, web log, and filter policy has to pass a higher test: not just that it is effective, but that it is necessary, justified, and will hold up under scrutiny.
Data minimisation and purpose limitation
Administrators and leaders in the California school system aren't just expected to filter harmful content; they are also expected to collect and use student data responsibly with restraint and purpose.
Key requirements under the California Consumer Privacy Act (CCPA) and the Student Online Personal Information Protection Act (SOPIPA) are clear:
Collect only what’s necessary to enforce your internet safety policy
Use it only for that purpose
Set a clear retention policy and delete data when it’s no longer required
This means you can't just install an agent-based student online safety solution on every school device and start recording everything kids do on their computers. You can't just log every click, every screen, and every message 'just in case' (I mean, technically you could, but good luck justifying that to a parent, a lawyer, or a data request from the state).
Student data privacy and consent requirements for California school districts
Before any type of online monitoring begins, schools in California must:
Inform parents and guardians of exactly what data will be collected in the process of monitoring
Clearly explain why the data is being collected, and how long it is retained
Provide access, correction, and deletion rights
Ensure any data sharing with vendors is clearly described in contracts, in line with California Education Code §49073.1 (AB 1584). Parents must be informed how student information is collected, used, and retained.
Even with good intentions, failure to meet these consent and transparency obligations can trigger fines, lawsuits, or a loss of trust that’s hard to rebuild.
Demonstrating CIPA compliance in California Schools
For schools making a funding request to E-Rate for the first time (The First Funding Year, they must demonstrate that they are in compliance with CIPA or are currently undertaking actions to comply with CIPA. Those “undertaken actions” aren’t symbolic. They must be documented steps that demonstrate your district is moving toward full compliance with CIPA’s requirements for filtering, monitoring, and a formal Internet Safety Policy.
Practical ways to demonstrate CIPA compliance progress
Below are examples of evidence that show a school or library is taking real steps toward CIPA compliance:
A published school board or library board agenda that lists CIPA compliance as a discussion topic
A staff meeting agenda showing CIPA compliance or filtering policy review
A quote from a service provider or vendor outlining technology protection measures (such as web filters or monitoring tools)
A draft Request for Proposal (RFP) or procurement document seeking bids for a filtering or monitoring solution
Meeting minutes or agendas from a public session where an Internet Safety Policy was discussed
Board meeting minutes (public or closed) where procurement or technology protection measures were reviewed
An internal memo from staff outlining CIPA-related gaps in an existing Acceptable Use Policy
A report or memo summarising research into suitable filtering or monitoring tools
A review or analysis comparing your Internet Safety Policy with those used by other districts or libraries
These don’t need to be glossy or overproduced. The point is to demonstrate due diligence and progress. If it shows that you’ve considered, documented, and discussed how your school protects students online, it counts toward compliance.
Keeping Students Safe Online without Over-Blocking or Overspending
Web filters are now standard across nearly all K-12 schools, helping districts meet CIPA’s requirement to block access to harmful or obscene content. But they’re not without issues. Research and surveys consistently show that many teachers and students feel web filters hinder academic work, often blocking legitimate educational material alongside harmful content.
Students regularly encounter restrictions when researching sensitive or controversial topics such as sexual orientation, reproductive health, or racial inequality, topics that can be vital to curriculum work or student wellbeing. This has led to a perception that schools are censoring rather than safeguarding, and that compliance has come at the cost of genuine learning.
Beyond blanket blocking
CIPA compliance doesn’t mean shutting down access. It means ensuring that when something harmful appears, it’s detected, logged, and addressed appropriately. The more innovative approach is to leverage your existing firewall’s visibility, not to create new walls, but to generate context-driven alerts and audit-ready reports that show intent, not just activity.
Why start with your firewall
Most California school districts already maintain enterprise-grade firewalls such as Fortinet, Palo Alto Networks, Sophos, or WatchGuard. These are essential for protecting staff and students against ransomware, phishing, and network intrusions, and they already capture the network data required for CIPA monitoring.
So why add another costly, cloud-based agent or monitoring tool to your tech stack?
With Fastvue Reporter, you can leverage the firewall you already trust to deliver intelligent safeguarding insight, without installing invasive software on every student device or sharing data with third-party vendors.
Note: Each firewall must be properly licensed and configured to log web traffic in compliance with district policy and vendor documentation.
Intelligent, privacy-aligned internet usage monitoring
Fastvue Reporter connects directly to your firewall, analyses the logs locally, and turns them into real-time alerts and clear, visual reports. Instead of blanket blocks, it identifies risk patterns, from self-harm searches to violent or explicit content, while preserving access for legitimate research and trusted mental health support sites.
The result is a monitoring and reporting system that is:
CIPA-compliant: providing active filtering and monitoring for E-Rate audits
Privacy-conscious: data stays on-premises, under district control
Budget-smart: no redundant licences or per-device agents
Educationally balanced: visibility without censorship
Fastvue Reporter gives California school districts what they actually need: intelligent filtering, transparent monitoring, and complete control over student data, all built for the firewall infrastructure they already have and fund.
Don't take our word for it. Try for yourself.
Download Fastvue Reporter and try it free for 14 days, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn