Reporting on WannaCry Ransomware Infected Machines
by

Scott Glew
To follow on from my previous post on how to create real-time alerts to detect WannaCry infected machines, this article describes how to run historical reports using Fastvue Reporter for SonicWall to find machines that have potentially been infected by WannaCry Ransomware.
The first and second variations of WannaCry ransomware access the following domains respectively:
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
You can therefore run a report on all machines that have accessed these domains using Fastvue Reporter for SonicWall.
Fastvue Reporter has three main reports, Overview Reports, User Overview Reports and Activity Reports. You can learn about the differences between the reports here. In this situation, we do not want to run a report on a specific user, so Overview Reports and Activity Reports are the most useful for identifying WannaCry Ransomware infections.
Overview Reports on WannaCry Ransomware Infections
Let's start by running an Overview Report on the domains that WannaCry Ransomware accesses:
-
Go to Reports | Overview Report and click the Filter button.
-
Select the Filter: Site Domain 'Equal to' iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com AND Site Domain 'Equal to' ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
-
To avoid having to specify the filter again in the future, click the Save Filter button and save the filter as 'WannaCry Ransomware'
-
Select the Date Range you want to run the report on, and click Run Report (note, only data that has been imported into Fastvue Reporter will be reported on. See Settings | Data Storage for information on the dates available to report on)
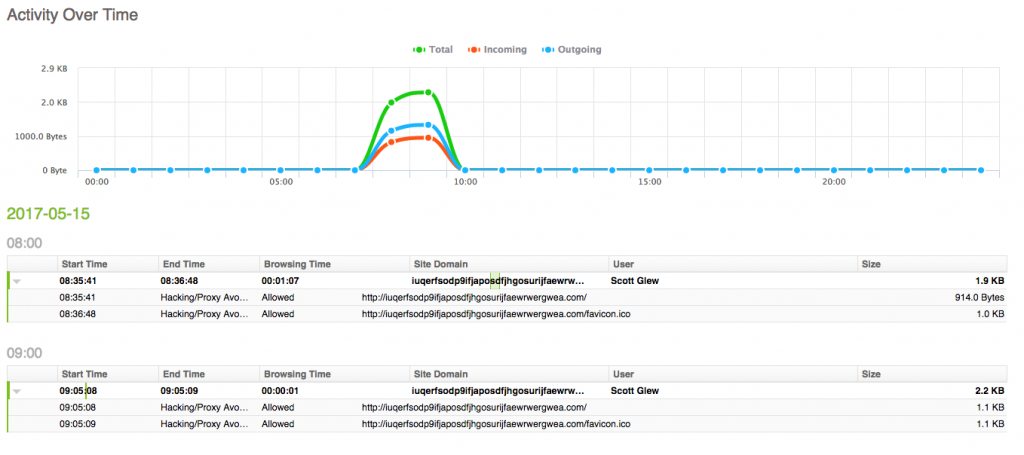
The Overview Report will show you the Top Users that have accessed the WannaCry Ransomware kill switch domains, along with Source IPs, SonicWall Actions and more.
Activity Reports on WannaCry Ransomware Infections
Now let's run an Activity Report to get more details on exactly when the WannaCry Ransomware domains were accessed, and what the full URLs were.
-
Go to Reports | Activity Reports
-
The Filters interface is already shown as Activity Reports require you to enter at least one filter. As we saved the filter for WannaCry Ransomware when running the Overview Report above, click the Load Filter button and select the WannaCry Ransomware filter. Then delete the default and currently blank/invalid 'Origin Domain' filter
-
Again, select the date range you want to run the report on and click Run Report
The Activity Report shows each individual session to the WannaCry Ransomware kill switch domains, including the user, start time and end time. Click the rows in the report to expand each session to view the full URLs, timestamps, and SonicWall Action.
Note: Note the URLs to the favicon.ico file above that occur a few seconds after the first hit to the domain. When testing, I was simply browsing to the WannaCry kill switch domains in my web browser. I wasn't actually infected with WannaCry Ransomware. If you see accesses to the favicon.ico file, this is a good indication that the clients are not actually infected, and were just browsing to the domains using a web browser as most web browsers automatically try to access the favicon.ico file.
Whitelisting WannaCry Ransomware's Kill Switch Domains
Don't freak out if you see SonicWall has allowed these URLs. This is actually the desired result, as the WannaCry Ransomware will install itself if it cannot access these URLs.
However, as the report above shows, SonicWall currently categorizes the WannaCry kill switch URLs as Hacking/Proxy Avoidance Systems. Fortunately, I was allowing this category in SonicWall's CFS feature, so these URLs were not blocked.
If your organization is blocking this category (and for good reasons!), you should either whitelist these kill switch domains, or re-categorize them into an allowed category for extra protection (SonicWall's Gateway Security Services already block the malware - see SonicWall Protects Customers from the Latest Massive WannaCry Ransomware Attack).
To whitelist the domains in SonicWall SonicOS 6.2.7:
-
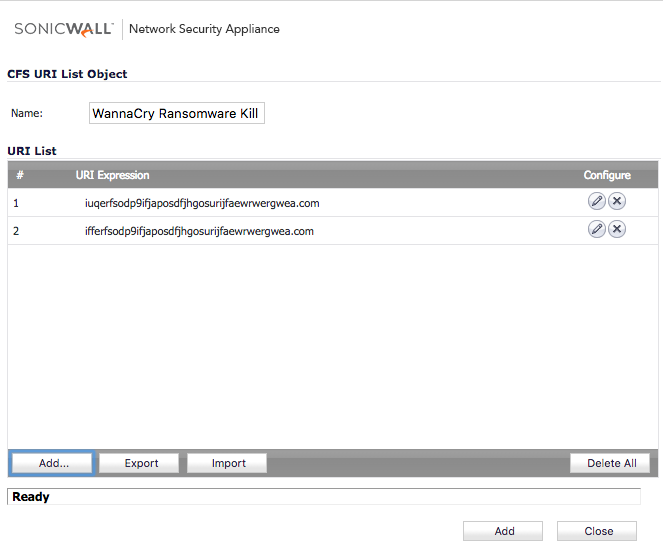
Go to Firewall | Content Filter Objects
-
Under URI List Objects add the WannaCry Ransomware kill switch domains to an existing whitelist or create a new object.
-
Under the CFS Profile Objects section, edit the profile that currently blocks the Hacking/Proxy Avoidance Systems category, and ensure your whitelist is selected in the Allowed URI List drop down list
Alternatively, go to Security Services | Content Filter and under the CFS Custom Category section, add a custom category (override) for the two kill switch domains, and select a non-blocked category such as Information Technology / Computers.
Limitations
The reports described above only report on the domains that the first two variations of WannaCry Ransomware attempt to before the installation phase (see here for more information on how the WannaCry ransomware kill switch domains work).
However, there is already a new variation that does not make any requests to a kill switch domain, which the above reports will not pick up on. So please make sure all your machines are patched, and legacy Operating Systems are updated. See Microsoft's Customer Guidance for WannaCrypt Attacks.
Whatever you do, do not block these domains on your SonicWall. Make sure they are whitelisted as described above.
Summary
As mentioned in the previous article, Fastvue Reporter does not block WannaCry Ransomware (or any malware) itself, but it does provide the visibility needed to effectively manage your SonicWall firewall and ensure the security of your network and users.
If you have SonicWall's Gateway Security Services correctly applied across all your networks, then hopefully your network has remained unscathed in this recent ransomware attack. If the reports above come back blank, that is a good thing!
To stay on top of any future incidents that may occur, we also recommend creating a real-time alert to detect WannaCry infected machines.
Good luck!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Reporting on WannaCry Ransomware Infected Machines
SonicWall DPI-SSL Logging Issues Affecting Bandwidth Reports